Dark web

Dark web, Deep web and some misconceptions about them WHAT IS THE DARK WEB? The dark web is a part of the web that isn’t filed via web indexes. You’ve presumably heard discussion of the “dark web” as a hotbed…


Security | Privacy | Compliance


Security | Privacy | Compliance

Dark web, Deep web and some misconceptions about them WHAT IS THE DARK WEB? The dark web is a part of the web that isn’t filed via web indexes. You’ve presumably heard discussion of the “dark web” as a hotbed…
Introduction The metasploit is a computer security project that provides information about security like vulnerability and penetration testing. It is most widely used in vulnerability scanning and exploitation. The metasploit framework is the most potent tool that cyber criminals and…

Is Biometrics Secure Biometrics are used everywhere. Biometrics are becoming an important part of our life, we use it everywhere, from smartphones to smart houses, from private offices to schools and businesses, and many other places where there is a…

HEALTHCARE CYBERSECURITY Healthcare cybersecurity is an essential basic for any association in the clinical business. It ranges from medical care suppliers to guarantors to drug, biotechnology, and clinical gadget organizations. It includes different measures to shield associations from outer and…

TOP 10 CYBERSECURITY THREATS EVERY BUSINESS MUST KNOW With the ever-evolving technology, new cybersecurity threats emerge almost daily. The consequences of a Cybersecurity threats caused security breach bring about critical harm to businesses of all sizes. Cyber threats are common…

In this article we will be diving deep about this interesting topic Red Teaming. But before that, let us see what this Red Teaming really means ! Defining the Red Team Red Teaming is actually a group of penetration testers who…
In this article we will be diving deep about this interesting topic Top Vulnerability Management Solutions. Now, let us see what it means ! Vulnerability management software: What is it ? – Common cybersecurity tools like firewalls and…
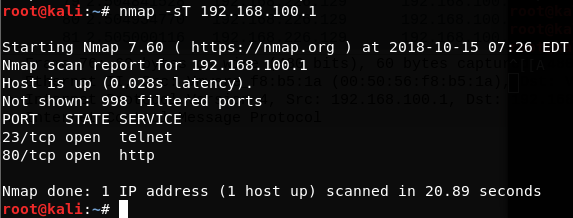
In this article we will be diving deep about this interesting topic Vulnerability Assessment & Penetration Testing (VAPT).But before that, let us breakdown VAPT and see what it really means !Let us now understand what a vulnerability means. Vulnerability It…
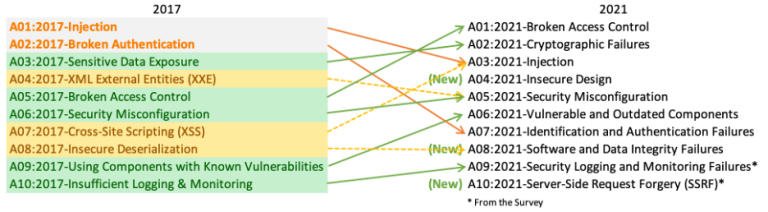
In this article we will be diving deep about this interesting topic Web Application Audit. But before that, let us see what this Web Application Audit really means ! Defining the Web Application Audit The auditing looks for the security…