Introduction
The metasploit is a computer security project that provides information about security like vulnerability and penetration testing. It is most widely used in vulnerability scanning and exploitation. The metasploit framework is the most potent tool that cyber criminals and ethical hackers can use to search for network and server vulnerabilities. The metasploit can be used in both legitimate and unauthorized activity.
A metasploit framework is a tool that is used to gather information exploitation, scanning, etc.
History
- Metasploit was created by H.D. MOORE in 2003. As a portable network tool used by Perl. The metasploit framework had been completed written in ruby and on 21st October 2009. And the repository Github It’s developed by rapid7 LLC, a security company that provides the undefined vulnerability management system.
Metasploit has two editions: –
- Metasploit Pro: – Its commercial version supports the automation and management of tasks. The commercial edition, which includes the express and community, is available to users who perform the web interface penetration test. Some additional features are unavailable in the Metasploit framework.
- Metasploit Framework: – An open-source edition work from with the command line. An open source that performs penetration testing and development tools.
MODULES OF METASPLOIT
- Exploits: – Tool is used to take advantage of weak systems. In the metasploit, there is currently over 2000..
- Android
- Window.
- Payload: In payload, there is a simple script for hackers to utilize to interact with the hacked system. In the metasploit currently 592 payloads. There are three different categories under the payloads:
- Command shell: There is a user to run a specific command against the host.
- Static payloads: In static payloads there is fixed/static of ip address and port number. For communication between the host and the client side of payloads.
- Dynamic payloads: – There is a user to save the anti-virus defense by generating unique payloads.
A few payloads are:-
- Singles: – In single payloads are self-contained and not connected to anything. It is just like a fire payload and forgets the payload.
- Stagers: – It is a responsible connection channel between metasploit and the targets.
- Stages: – Stages are the payload component and it is downloaded by stagers.
- Listeners: – It is Bad software that covers the obtained access.
- Encoders: – It is Used to convert the code.
- Auxiliary: – It is extra tools and commands. In this module the metasploit framework has hundreds of the auxiliary modules performing the scanning, the fuzzing, the sniffing, and much more, etc. Although this module does not give you the shell, it shall be helpful in the penetration timing.
There are divided in three categories: –
- Admin:- In admin they further divided into some categories: –
- Admin HTTP Modules.
- Admin MSSQL Modules.
- Admin MySQL Modules.
2. Scanner: – In Scanner they further divide into:
- SSH.
- POP3
- HTTP
3. Server: – In server they divided one category: –
- Server Capture Module.
- Nops: – It is (No operation) and does nothing.
The main components of the metasploit framework can describe below: –
- msfconsole: – It is the main command of the line interface to access and work with the metasploit framework. In console lets you do scan the targets, vulnerability and exploit the weakness
- Exploit module: – It is allowing the tester to target the specific vulnerability. Metasploit has large no exploit modules like SQL injections and buffer overflow.
- Tools: – In this component we have used tools to search like vulnerability or penetration testing.
Some basic commands in metasploit are: –
- help: – In this command show every available command in the msfconsole.
- info: – It is showing the description of the exploit, or it provides the details of the exploit.
- search: –If you have any idea about what you are looking for you can use the search command.
- set: – It Sets a context-variable for specific value.
- unset: – It has just removed all the set values.
- unsetg: – It has just removed all the set values.
- setg: – It is just set a global way.
- back: – In this command to exit from the current context.
- exit: – In this command to exit the console.
- grep: – In the command grep the output of another command.
- show: – In command displays the module of a given type or all values.
- use: – In the use command in select the module by the name.
How to get the metasploit
Metasploit is available as an open-source installer directly from the rapid7 website. it comes pre-installed in kali and Parrot. But it can be downloaded into other os as well
METERPRETER
Meterpreter is a metasploit attack payload that provides the interactive shell from which an attacker can explore the target machine and execute code in the payload.
Meterpreter is an advanced payload used in memory dll (dynamic link libraries (contain code and data that can be used again and again by the same program)) stager. It is communicated over with the stagers sockets and provides a comprehensive client-side ruby API. As a result, the meterpreter resides in memory and writes nothing to disk.
Meterpreter design goals: –
- Stealthy: – In meterpreter resides in the memory and nothing is written on disk, and it is defaulted by meterpreter used by the encrypted communications process.
- Powerful: – In the powerful goals meterpreter is used to communicate.
- Extensible: – In Extensible new features can be added in meterpreter without having to rebuild (meterpreter) it.
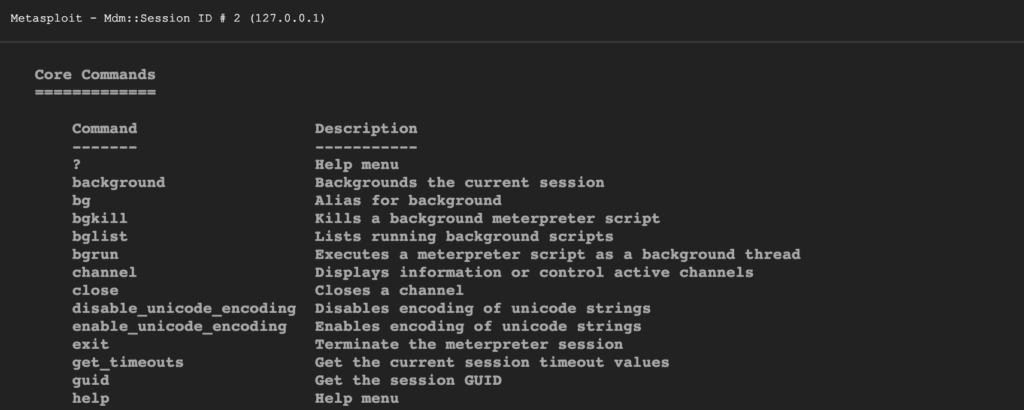
Some basic commands of metasploit are: –
- help: – It just displays the meterpreter menu.
- background: – It sends the current meterpreter session in the background.
- cat: –It displays the content of the file.
- clear: – It just clears the window or terminal.
- download: – In this command download the file from the remote machine.
- getduid: – In this command show the user.
- ipconfig: – It is just showing the network interface and address on a remote machine.
- ps: – In this command show the list of running processes targeted.
- execute: – In this command, we run a command on the target.
- edit: – In this command, we open the file located on the host targeted.
Please visit our Services page for a full range of services offered.