Earn the trust of your customers and showcase your dedication to data security by utilizing our dependable SOC 2 audit services.
A SOC 2 (Service Organization Control 2) audit is a type of audit report that assesses a service organization’s controls over its customers’ data. This audit is conducted by an independent third-party auditor and is based on the American Institute of Certified Public Accountants AICPA Trust Services Criteria. SOC 2 audits are essential for service organizations that handle sensitive information, such as financial or personal identifiable information PII.
The audit report serves the purpose of demonstrating the effectiveness of the organization’s controls, and customers often requests for it as a part of their due diligence process.
The audit report consists of several key components.
- It includes a description of the organization’s system operation and processes.
- It provides an evaluation of the design and operating effectiveness of the controls.
- Lastly, it highlights any identified control deficiencies or areas for improvement.
Moreover, the primary aim of the report is that the organization’s customers and stakeholders could utilize it. Thus, they can assess the security and reliability of the services provided.
It is important to note that SOC 2 audits are tailored to the specific service organization being audited and the services it offers. For example, a cloud service provider may undergo the audit specifically for its cloud infrastructure services, excluding other areas such as HR or accounting services. Additionally, the scope of the audit can be customized to align with the unique requirements of the organization and its customers.
These audits serve as a vital tool for service organizations as they demonstrate their commitment to data security. Moreover, it helps to provide assurance to their customers regarding the handling of their confidential information in a secure and reliable manner. Having a SOC 2 audit and receiving a favorable audit report, helps a service organization in gaining competitive advantage. Therefore, they may build trust with their customers.
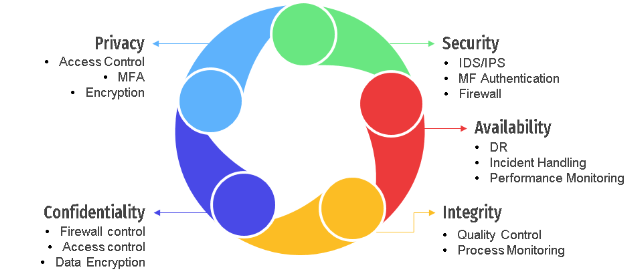
SOC 2 Pillars
Benefits of SOC 2
Increased customer trust:
A SOC 2 compliance assessment demonstrates that the service organization takes data security seriously. It shows the organization has implemented sufficient measures to protect customer data against unauthorized access. Thus, it can boost client trust and confidence in the company’s offerings
Competitive advantage:
Having a SOC 2 audit report can provide service organizations with a competitive advantage in the marketplace. Many customers and potential business partners may demand the report as part of their due diligence process. Consequently, a readily available SOC 2 report can help the organization attract new business opportunities.
Improved internal controls:
The audit process helps service organizations identify areas for improvement in their internal controls. This, in turn, leads to improved information security and more efficient corporate procedures.
Reduced risk of data breaches:
Implementation of the controls recommended in the SOC 2 audit report can help service organizations in mitigating the risk of data breaches and other security incidents. Furthermore, this proactive approach helps safeguard the organization’s reputation. It also helps mitigate potential legal and regulatory complications.
Increased transparency:
The audit report offers transparency into the organization’s data security practices and contributes to building trust with stakeholders. This is particularly significant for service organizations that handle sensitive data or must comply with regulatory requirements.
Types of SOC 2 Report
SOC 2 audits are conducted to evaluate a service organization’s controls related to security, availability, processing integrity, confidentiality, and generally accepted privacy principles GAPP. There are two types of services that can be audited under SOC 2: Type 1 and Type 2.
SOC 2 Type 1:
In a SOC 2 Type 1 report, the auditor evaluates the design and implementation of controls at a specific point in time. The auditor reviews the controls and provides an opinion on whether they are suitably designed to meet the relevant common criteria.
SOC 2 Type 2:
In a SOC 2 Type 2 report, the SOC analyst evaluates the design, implementation, and operating effectiveness of controls over a period of time, typically six months to a year. The SOC analyst reviews the controls and provides an opinion on whether they were suitably designed and operating effectively throughout the period under review.
Both Type 1 and Type 2 reports are useful for service organizations, depending on their needs. A Type 1 report can assure customers that the service organization has appropriately designed its controls to meet their needs. On the other hand, a Type 2 report provides additional assurance that the controls are operating effectively over time.
Our Methodology
Planning:
The auditor collaborates with the service organization to determine the scope of the audit, which includes identifying the systems and processes to be evaluated, as well as the relevant trust service principles such as security, availability, processing integrity, confidentiality, and privacy. Furthermore, the auditor reviews the service organization’s documentation and policies that pertain to the controls being evaluated.
Testing:
The auditor conducts testing to assess the design and effectiveness of the controls in place. This may involve reviewing documentation, interviewing personnel, and conducting system walkthroughs.
Reporting:
The auditor delivers a report that contains an opinion on the effectiveness of the controls, considering the applicable trust service categories. The report also encompasses any identified control deficiencies and recommendations for improvement.
Follow-up:
The service organization resolves any identified control deficiencies and implements the auditor’s recommendations for improvement. The auditor may conduct follow-up testing to verify that the deficiencies have been remedied.

