How to Prepare for a Cyber Security Internship

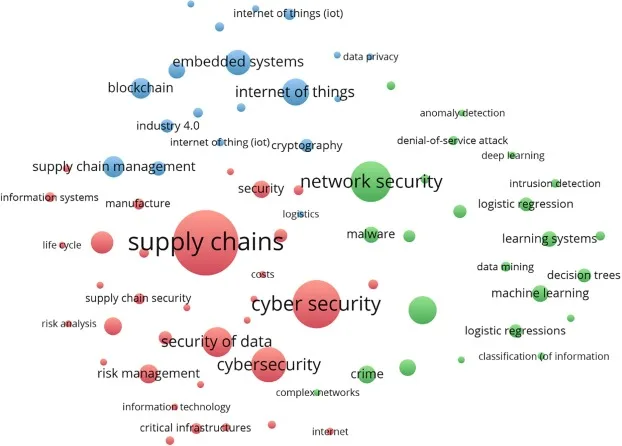
cyber security internship 1. Hands-on experience: An internship in cyber security will provide you with real-world experience in a professional setting. This will help you apply the theoretical knowledge you have gained in the classroom to actual scenarios and challenges.…