
What is Red Team?
Red team is group of professionals who emulates hacker’s methodologies and conduct a security assessment for an organization and provide them security feedback. They are also known as Ethical Hackers. Their methodology is not only limited with only penetration testing but also contains techniques like social engineering, privilege escalation and more. Awesome red teaming is a simulated cyber attack exercise that helps organizations test and improve their security defenses by adopting an adversarial perspective.
Cyber Chain kill
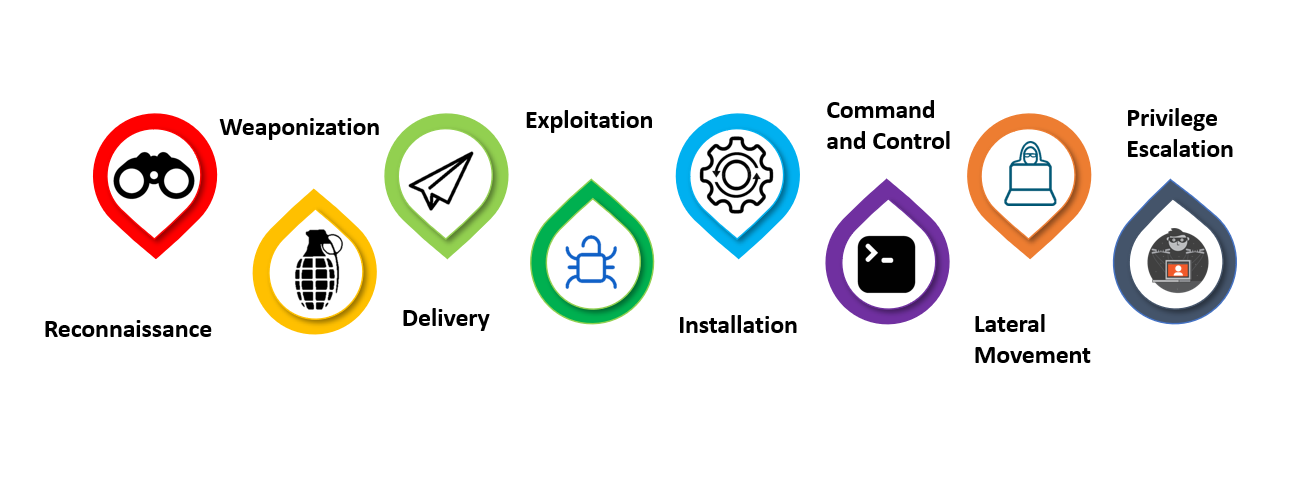
It is a series of step that a hacker performs to launch a successful attack. The methods and some of the tools along with their uses are mentioned below:
Reconnaissance: – There are various techniques for discovering without active involvement such as using whois information, using way back machine, techniques such as dorking, social media accounts, harvesting email addresses gathering info from breaches, using search engine likes shodan to gather more information
This step includes for active involvement are like determining the network range, enumerating active directory information, services running in the system.
Weaponization: – a hacker only needs one attack vector to be successful. Therefore, security is only as strong as its weakest point and it’s up to you to discover where those potential attack vectors are.
Delivery:- after gaining access a hacker need to deliver the payload into the right environment to exploit further and cause a persistent connection between the victim
Exploitation:- The exploitation of a system begins, depending on the type of attack. As mentioned before, some attacks are delayed and others are dependent on a specific action taken by the target, known as a logic bomb.
Installation :- This includes a backdoor or a remote access to provide on an attacker’s machine.
Command and Control:- an attacker will take control of systems and execute whatever attack they have in store for you.
Lateral Movement:-Attackers will move from system to system, in a lateral movement, to gain more access and find more assets.
Privilege escalation :-It is the method of exploiting a bug to gain higher access to a resource.
More about Red Teaming
- Compliance and Governance: Evaluate the cloud environment’s compliance with relevant regulatory requirements and industry standards. Compliance with regulations such as the General Data Protection Regulation (GDPR), the Payment Card Industry Data Security Standard (PCI DSS), and any other relevant frameworks is part of this.
- Cloud Provider Evaluation: If applicable, assess the cloud service provider’s (CSP) security procedures. Examining the CSP’s security certifications, contractual duties, data protection policies, and incident response capabilities is part of this process.
- Reporting: In a detailed assessment report, document the findings, vulnerabilities, and recommendations. The report should include a prioritised list of vulnerabilities based on severity, as well as proposed mitigation techniques and concrete initiatives to improve cloud security.
- Social Engineering: Use a variety of social engineering tactics to manipulate employees and acquire unauthorised access. Phishing emails, pretexting phone calls, physical access attempts, and other forms of deceit can all be used to exploit human vulnerabilities.
- Network and Infrastructure assaults: Simulate network and infrastructure assaults to detect weaknesses and potential entry points. This can include network scanning, misconfigurations, known vulnerabilities, or attempting to circumvent security restrictions.
- Web-based and application-based attacks: Examine the security of the company’s apps and web services. Vulnerability scanning, penetration testing, injection attacks (e.g., SQL injection, cross-site scripting), and attempting to acquire unauthorised access or escalate privileges are all examples of this.
- Physical security testing involves determining the efficiency of physical security measures such as access controls, surveillance systems, and security protocols. Attempting unauthorised access to restricted locations, tampering with physical devices, or exploiting holes in physical security mechanisms are examples of such actions.
- Wireless Network Testing: Evaluate the organization’s wireless network infrastructure’s security. This includes locating wireless access points, testing for weak encryption, spying on wireless networks, and trying unauthorised access.
- Activities Following Exploitation: After gaining access, replicate post-exploitation activities to put the organization’s incident response capabilities to the test. This could include lateral network movement, privilege escalation, data exfiltration attempts, or persistence measures to keep access.
- Reporting and debriefing: In a complete report, document the results, techniques utilised, vulnerabilities exploited, and suggestions. Provide a thorough analysis of the red teaming exercise, including identified flaws, potential consequences, and actionable recommendations to strengthen the organization’s security defences.
- Remediation and follow-up: Collaborate with the organisation to resolve the vulnerabilities and weaknesses that have been found. This involves advising on risk mitigation, upgrading security controls, performing security awareness training, and establishing an incident response plan based on the exercise’s lessons learned.
Unlock the possibilities today! Explore our wide range of services and get in touch with us at Contact us or email us at [email protected] to discover how we can cater to your needs.
You can also call us at +971-487-441-45 or whatsapp
Top 10 Red Team Assessment Company
Introduction
In an increasingly digital world, the importance of robust cybersecurity measures cannot be overstated. As businesses and organizations embrace technology to streamline operations, they also become vulnerable to cyber threats and attacks. Red team assessment companies play a critical role in safeguarding these entities by simulating real-world attacks and identifying vulnerabilities before malicious actors can exploit them. we’ll delve into the realm of cybersecurity and explore the top 10 red team assessment companies that are at the forefront of securing digital landscapes.
What is Red Teaming?
Red teaming or red team assessment is an exercise involving a group of Cyber Security experts also known as ethical hackers empowered to initiate attacks from real-world adversaries in order to test and challenge an organization’s security posture.
Red Teaming Assessments are driven by a specific goal, in this experts pretends to be an enemy, imitate the actions/behaviors of real attackers, adopts various strategies, techniques and procedures (TTPs), exploits potential vulnerabilities, infiltrates systems, networks, etc., and invades the network & users of the target organization.
Red teams create precise scenarios that closely resemble threat actors or Real world Attackers. Red Team Assessment uses a combination of social engineering, phishing, and other sophisticated methods to slowly but eventually gain unauthorized access. Overall, the goal of a red team is to utilize a comprehensive, dynamic approach to identify gaps and vulnerabilities, assess the effectiveness of existing security controls, and provide organizations with actionable insights to strengthen their defenses and improve the overall Security posture.
How is Red Teaming Different from Penetration Testing?
Red teaming and penetration testing are security assessment techniques that launch attacks on an organization’s security infrastructure to test its strength and identify vulnerabilities. However, the methods, and objectives of the two differ.
Penetration testing is the practice of testers using various tools and techniques to identify vulnerabilities in a company’s IT infrastructure. The main goal of penetration testing is to identify as many vulnerabilities as possible in a system, network or application in a short period of time. Therefore, it mainly follows a predefined structured approach to eliminate vulnerabilities.
On the Other Side, Red teaming Exercises are more complex and technical. It imitates real attackers with no time limit and conducts a thorough, in-depth security posture testing exercise. The main goal of a red team assessment is to ultimately gain access to specific data, folders, or systems that are predetermined by a team within an organization. Therefore, a red team assessment is specifically designed for the test objective, regardless of the duration of the attack, the team applies all tactics the attacker intends to apply to the organization’s internal security personnel and controls to achieve the objective.
Overall, red teaming is more comprehensive than penetration testing because it tests the strength of an organization’s security culture, not just its systems.
Top 10 Cybersecurity Red Team Service Providers
Now that we have cleared about concepts around red teaming and its effectiveness over penetration testing, let’s highlight the best ten cybersecurity red team service providers you can choose from:
1. Eshield IT Services
First on our list and the top contender for the Red teaming service provider is ESHIELD. Known for its exceptional expertise and commitment to delivering unparalleled results, ESHIELD IT offers the most comprehensive and powerful red team assessment services.
ESHIELD’s Red Team Security Exercise uses meticulously crafted framework for a real-world exercise, strategically honing the organization’s capacity to effectively identify, track, isolate, and remediate potential breaches. It incorporates a multi-phased comprehensive red team assessment approach involving intelligence gathering, external operations, internal operations, onsite operations (optional), and reporting. Below are the key features of ESHIELD Security red team service:
· Scoping tailored as per specific organization, environment and objectives.
· Provides Proof of Concept, demonstrating manual testing efforts along with detailed findings to provide comprehensive insights.
· Multiple spear-phishing engagements with active payloads.
· Comprehensive external, internal, and onsite operations to detect and exploit vulnerabilities from various attack vectors.
· Accurate and closest replication of real-world cyber threats.
· Collaboration with the organization’s internal team.
· Detailed reporting with actionable recommendations.
· Access to other additional services, such as network/application penetration testing, OT network (SCADA/ICS) testing, cloud Security, etc.
In short, Eshield’s commitment to delivering state-of-the-art services and offering a highly-skilled red team makes it stand out as a leading and one of the best cybersecurity red team service providers.
2.Crowdstrike
Crowdstrike is another reputed name in the cybersecurity red team services list. It is one of the best EDR product company but they do have services for Red Teaming. It is known for its intelligent real-world adversary tests to reflect the organization’s capability to withstand a real-life attack. Its red teaming service provides organizations with a clear understanding of their security posture and strength against defending specific assets from threat actors.
Crowdstrike’s red team uses a wide range of composite attack vectors to identify exploitable security holes. The red team chains together cross-domain or seemingly separate vulnerabilities to get a holistic view of team behavior, software, networks, applications, etc. Below are the key features of Synopsys’s red team service:
· Simulates real-world targeted attacks.
· Wide range of attack surfaces, such as penetration testing, social engineering, reconnaissance, etc.
· Looks and uncovers various risks such as sensitive data written to log files, encryption keys in source code, Personally Identifiable Information (PII), etc.
· Strategic recommendations to focus on risk areas and further improvements.
In short, Crowdstrike’s red team service is another effective and powerful service for organizations to test out their security strengths and improve their security posture.
3. CyberArk
CyberArk‘s Red Team specializes in adversary simulations, where the company’s seasoned and ethical hackers think like seasoned attackers and conduct attacks to uncover any potential vulnerabilities. Cyber Ark is known for their PAM product. They leverage an organization’s hybrid and cloud environments, processes, DevOps pipelines, and any other critical systems an attacker can target.
CyberArk’s Red Teams use various types of Tactics, Techniques, and Procedures (TTPs) to exploit all means used by attackers to discover known/unknown threats/vulnerabilities, test existing security practices, and identify areas for improvement field. Here are the key features of CyberArk Red Teaming Services:
· As with attackers, use any means necessary to test the organization’s security posture.
· Work with the organization’s internal teams to set program goals.
· A two-part report summarizing the assessment and technical analysis to identify issues and recommendations.
In short, CyberArk is another trustworthy red team services provider that can help organizations uncover vulnerabilities and improve their threat detection and response capabilities.
4. Redscan
Redscan has a dedicated team of red team operations professionals who take a systematic and comprehensive approach to thoroughly assess an organization’s threat detection and response capabilities. They use the latest hacking tools and techniques to simulate custom-made cyber attacks and test the robustness of an organization’s security.
To achieve its testing goals, Redscan takes a “no-compromise approach”. The team first gathers information on successfully compromised targets. Experts then launch attacks based on the vulnerabilities they find. Once this is done, the team launches an attack and attempts to gain a foothold in the target network. After the team has successfully established itself, there are more internal compromises to make. In this way, Redscan ensures a thorough assessment and produces a comprehensive final report. The following are the key features of the Rescan red team service:Uses a wide range of intelligence-led evasion, deception, and stealth techniques
· Customized assessment according to the agreed objective.
· A high-level overview of the whole assessment.
· Detailed technical feedback.
In short, Redscan’s highly expert team of ethical hackers and multi-blended attack methods make it another best cybersecurity red team service provider.
5. Stage 2 Security
Stage 2 Security provides Red Team-as-a-Service (RTaaS) service to organizations for comprehensive and continuous assessment of their entire IT infrastructure. Whether an organization wants to conduct red team assessment for cloud, web applications, IoT, insider threat, or external threat, RTaaS covers everything.
S2 RTaaS helps organizations have a personalized red team that facilitates continuous adversary emulation, focusing on achieving mission objectives, such as external attack surface management (EASM), ransomware attack surface testing (RAST), etc. The team uses stealthy lateral movement techniques to move laterally within the environment to accomplish the objectives. The team even allows organizations to request focused engagements to fulfill specific engagement needs. Below are the key features of S2 RTaaS:
· Deploys human-validated, real-world attackers’ techniques, tactics, and procedures (TTPs).
· Customizes phishing exercises to closely emulate adversary tactics to test the weakest link.
· Provides findings about vulnerabilities through images or video demonstrations.
· Provide continuous training to the Blue Team.
In short, S2 RTaaS provides a non-stop adversary emulation that organizations need to keep their security posture up-to-date.
6. Praetorian: Empowering Cyber Resilience
Praetorian’s red team assessments focus on helping organizations become cyber-resilient. Their comprehensive evaluations identify weaknesses in people, processes, and technology, fostering a holistic security approach.
Conclusion: Fortifying the Digital Landscape
7. Mandiant: Strengthening Resilience Through Proactive Testing
Mandiant, a subsidiary of FireEye, is synonymous with cutting-edge cybersecurity solutions. Their red team assessment services involve simulated attacks and intricate evaluations of an organization’s security posture. By identifying weaknesses and providing actionable insights, Mandiant empowers businesses to enhance their defenses against emerging threats.
8.Rapid7: Pioneering Vulnerability Management
Rapid7 takes a comprehensive approach to cybersecurity by offering a suite of services, including red team assessments and penetration testing. Their expertise lies in identifying vulnerabilities across networks, systems, and applications, allowing businesses to mitigate risks effectively.
9.Cobalt: Harnessing the Power of Crowdsourced Security
Cobalt’s unique approach involves leveraging a global network of security researchers to perform red team assessments. This crowdsourced model enables organizations to tap into a diverse range of expertise, resulting in thorough assessments that uncover even the most hidden vulnerabilities.
10. NCC Group: Tailored Solutions for Optimal Security
NCC Group‘s red team assessments are tailored to meet the specific needs of each client. With a strong focus on simulating real-world attack scenarios, their assessments provide insights into an organization’s ability to detect and respond to sophisticated threats.
FAQ:
Q: What is a Red Team Assessment?
A: A Red Team Assessment is a security assessment methodology used to simulate a real-world cyber attack to identify security vulnerabilities and gaps in an organization’s security posture.
Q: How does a Red Team Assessment differ from a traditional penetration test?
A: While a traditional penetration test focuses on finding vulnerabilities, a Red Team Assessment goes a step further by simulating a real-world attack scenario to test an organization’s defenses against advanced persistent threats.
Q: What are the key objectives of a Red Team Assessment?
A: The key objectives of a Red Team Assessment are to test an organization’s security posture, assess physical security controls, evaluate application security, and identify security gaps that could be exploited by malicious actors.
Q: How does a Red Team Assessment benefit an organization?
A: Red teaming offers organizations the opportunity to improve their security posture by identifying weaknesses and areas for improvement that may not be apparent through traditional security assessments.
Q: What is the process involved in a Red Team Assessment?
A: The red team assessment process typically involves planning and reconnaissance, executing red team tactics to breach defenses, documenting security vulnerabilities, and presenting findings in a comprehensive sample report.
Q: How does a Red Team Assessment help in enhancing overall security posture?
A: By exposing vulnerabilities through real-world attack scenarios, a Red Team Assessment helps organizations assess their security posture and take necessary measures to improve their defenses against cyber threats.
Q: What is the role of the security team in a Red Team Assessment?
A: The security team collaborates with the red teamers during a Red Team Assessment to conduct a thorough assessment of an organization’s security posture and implement necessary measures to enhance security defenses.
Wrapping Up
Red teaming is a valuable assessment approach to enhance an organization’s overall cybersecurity resilience. Owing to that, it is increasingly recognized as a crucial component of proactive cybersecurity strategies. Therefore, if your organization is also looking to test the strength of its security landscape, then you can choose any of the above services for red team assessment. Out of all the above services, ESHIELD seems the best choice, as its exceptional expertise, comprehensive multi-phased approach, customized scenarios, advanced techniques, and non-stop collaboration make it a clear winner in the industry.
In an era dominated by digital transformation, the significance of red team assessments cannot be underestimated. As cyber threats evolve in complexity and scale, proactive evaluation of security measures becomes paramount. The top 10 red team assessment companies mentioned above have demonstrated their expertise in navigating the intricate landscape of cybersecurity. By partnering with these industry leaders, businesses and organizations can bolster their defenses, stay ahead of emerging threats, and cultivate a culture of cyber resilience in an ever-evolving digital landscapes.

