CLOUD SECURITY
It is a process of finding and solving the security flaws in cloud security. The sole purpose of this testing is to check the strengths and weakness of the cloud security.

Cloud Security Assesment
A cloud security assessment in Dubai seeks to assess the security of a cloud environment’s infrastructure, services, and customizations. The components of a cloud security assessment can vary depending on the assessment’s specific criteria and scope. However, the following are some common components that are usually included:
- Scope and Objectives: Clearly describe the scope of the assessment, including the specific cloud services or platforms to be evaluated, as well as the assessment objectives.
- Examine the general architecture of the cloud environment, including network design, virtualization technologies, data storage, and communication methods. This involves evaluating the efficiency of segmentation, network management, and overall cloud infrastructure security.
- Identity and Access Management (IAM): Examine the IAM controls and rules in place to manage user access and permissions in the cloud. This includes evaluating the efficacy of user authentication, authorisation techniques, multi-factor authentication (MFA), and the least privilege principle.
- Data Security: Examine how data is stored, processed, and sent on the cloud. This involves an examination of encryption procedures, data isolation, data classification, and access controls. Examine compliance with data protection standards and best practises in the sector.
- Network Security: Examine the security measures in place to safeguard the cloud environment against network-based assaults. Examining firewall configurations, network segmentation, intrusion detection/prevention systems (IDS/IPS), and distributed denial-of-service (DDoS) defence measures are all part of this.
- Logging and Monitoring: Examine the cloud environment’s logging and monitoring features. Examining logging setups, audit trails, security event monitoring, and incident response mechanisms are all part of this. Assess the efficacy of log analysis and threat detection techniques.
- Incident Response and Recovery: Examine the cloud-specific incident response and disaster recovery processes. This includes assessing the incident response strategy, backing up and restoring data, and testing the effectiveness of incident response procedures.
- Vulnerability Assessment and Penetration Testing: Perform vulnerability scanning and penetration testing to detect potential cloud vulnerabilities and weaknesses. Simulating real-world attack scenarios is one way to verify the effectiveness of security mechanisms and find areas for improvement.
- Compliance and Governance: Evaluate the cloud environment’s compliance with relevant regulatory requirements and industry standards. Compliance with regulations such as the General Data Protection Regulation (GDPR), the Payment Card Industry Data Security Standard (PCI DSS), and any other relevant frameworks is part of this.
- Cloud Provider Evaluation: If applicable, assess the cloud service provider’s (CSP) security procedures. Examining the CSP’s security certifications, contractual duties, data protection policies, and incident response capabilities is part of this process.
- Reporting: In a detailed assessment report, document the findings, vulnerabilities, and recommendations. The report should include a prioritised list of vulnerabilities based on severity, as well as proposed mitigation techniques and concrete initiatives to improve cloud security.
Benefits of performing Cloud Security Assessment in UAE
- Vulnerabilities: It can assist an organisation find vulnerabilities and shortcomings in its cloud infrastructure and services. It enables you to identify potential security vulnerabilities, misconfigurations, or faults that attackers could exploit.
- Risk Mitigation:It can help you better identify the possible hazards connected with your cloud environment. This knowledge enables you to successfully apply risk mitigation strategies and prioritise security measures.
- Compliance and Regulations: Many businesses have unique data protection and privacy regulation requirements, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA). Cloud security strategy services evaluation ensures that your cloud infrastructure complies with these standards, thereby avoiding legal and financial ramifications.
- Improved Data Protection: These evaluations aid in determining the efficacy of data protection techniques applied in the cloud environment. Encryption, access controls, data separation, and incident response processes are all part of this. You can improve the security and confidentiality of your data by fixing any flaws.
- Incident Response Preparedness: Assessments assist organizations in preparing for future cloud security incidents. Organizations can discover gaps, streamline processes, and develop a more robust incident response framework by analyzing existing incident response plans. In the event of a security breach, this assures a prompt and effective reaction.
- Cost Optimization: It can assist organizations in cost-cutting by identifying unneeded or redundant security procedures. Organizations can decrease costs while maintaining an appropriate security posture by simplifying security measures and eliminating overlapping or ineffective controls.
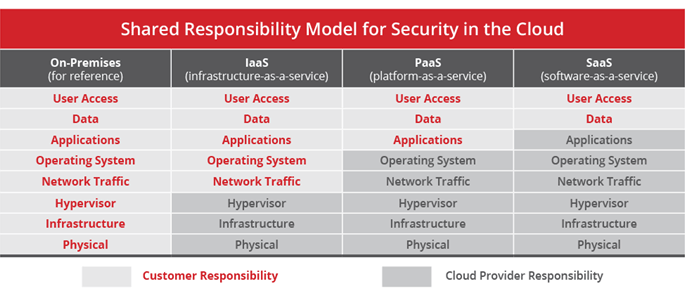
Cloud Responsibility matrix
Our Services
Cloud Security Assessment
Cloud Security Risk Assessment
Cloud Data Security
Cloud IAM
Cloud Penetration Testing
Best Practices to keep in mind:
1.Check the Service Level Agreement and make sure that proper policy has been covered between Cloud service provider (CSP) and Client.
2.To maintaining the Governance & Compliance, check the proper responsibility between Cloud service provider and subscriber.
3.Check the service level agreement Document and track the record of CSP, determine role and responsibility to maintain the cloud resources.
4.Check the computer and Internet usage policy and make sure it has been implemented with proper policy.
5.Check the data which is stored in cloud servers is encrypted by default.
6.Check the Two Factor authentication is used and validate the OTP to ensure the network security.
7.Check the SSL certificates for cloud services in the URL and make sure certificates purchased from repudiated Certificate Authority (COMODO, Entrust, Symantec, Thawte etc.)
8.Check the Component of the access point, data center, devices, using appropriate security Control.
9.Check the policies and procedure for disclose the data to third parties.
10.Check if CSP offers for cloning and virtual machines when required.
11. Check the proper input validation for Cloud applications to avoid web application Attacks such as XSS, CSRF, SQLi, etc.
12. To know more about Cloud security controls, use CCM

