
Secure your business operations in the UAE and protect your valuable data with our expert NESA compliance services.
NESA stands for the National Electronic Security Authority, which is a UAE government entity responsible for ensuring the security of electronic information and communication systems in the country. The primary goal is to protect critical infrastructure, such as banking, energy, transportation, and government entities, from cyber threats and vulnerabilities. NESA, a federal authority, is entrusted with safeguarding critical information infrastructure across the nation.
NESA develops and implements information security standards, policies, and guidelines. All entities in the UAE must adhere to these standards in order to maintain compliance with the regulations. Moreover, it is mandatory for all businesses, government agencies, and service providers operating in the UAE. It involves implementation of a range of technical and organizational security measures to ensure the confidentiality, integrity, and availability of information. By complying with these measures, entities in the UAE can ensure the security of their operations. Additionally, this proactive approach helps protect against cyber threats and maintain the trust of their customers and stakeholders.
Who must be NESA compliant?
All government organizations, semi-government organizations and business organizations that are identified as critical infrastructure to UAE must be NESA compliant.
What are the standards to follow to become NESA Compliant?
The UAE National Cyber Security Strategy (NCSS), developed and governed by NESA, defines the protection requirements of UAE Cyberspace. However, the primary standard to follow is UAE Information Assurance Standards (UAE IAS). Additionally, the NESA National Cyber Risk Management Framework defines its Risk Assessment process.
What are the NESA Security Control Implementation timelines?
In a prioritised way, UAE IAS lists 188 security controls. There are four stated priorities, and the controls are organised around these four goals. NESA anticipates that the entities will implement the Priority 1 controls as soon as possible. P2 to P4 controls will be added later. Despite the fact that no set dates are stated in the regulations, our experience suggests that the P1 dates are close.
P1 controls are largely management controls, with some technological security needs thrown in for good measure. It demands 35 controls among the 188 controls that assist organisations in establishing an information security foundation. These measures must be adopted by all relevant entities, regardless of the conclusion of the Risk Assessment.
How does NESA evaluate the compliance status?
According to the standards and based on the information, from the public domain. NESA would get involved through different approaches based on the implementation level at the operator.
Reporting:
NESA would collect and consolidate the reports from entities to generate sector and national risk contexts. These are based on the self-assessment reports prepared by the critical national infrastructure entities-
Auditing:
NESA may audit, by means of requesting evidence, the operator to validate some or all of the reported status of an entity. -
Testing:
The audits may be extended by testing specific control implementations at the operator.
More About NESA IA
The National Electronic Security Authority (NESA) in the United Arab Emirates manages and provides NESA IA. Moreover, the IAS Standards developed by NESA follow a threat-based strategy that assists organizations in implementing necessary security measures. Additionally, each security control mapping aims to mitigate the majority of the 24 identified risks. These risks were derived by NESA from multiple industry reports in 2012, which accounted for approximately 80% of the reported breaches.
According to the IAS standard, security controls are classified based on priority, ranging from highest (P1) to lowest (P4) importance. Furthermore, adopting a threat-based approach rather than an asset-based approach helps bridge the gap between IT Risk and Business Risk, making it a prudent choice. However, it is important to note that while NESA provides a comprehensive standard, it may not always offer protection against highly sophisticated attackers. Moreover, although it does not delve into specific activities related to each business, it covers the management and technical control sectors.
Benefits of getting NESA Compliant
Legal Compliance:
All businesses, government institutions, and service providers operating in the UAE must comply with NESA guidelines. Noncompliance with the regulations may result in fines, legal penalties, and other punishments.Business Continuity:
NESA compliance UAE requires enterprises and organizations to put in place procedures to ensure that operations continue in the event of a cyber-attack or other disruptive incident. This ensures that firms can continue to operate even if unexpected circumstances occur.Improved Risk Management:
In order to comply with NESA standards, businesses and organizations must identify, assess, and manage information security risks. This assists firms in better understanding the risks they face and implementing appropriate risk management procedures.Improved Security:
Businesses and organizations must comply with NESA by implementing security measures that safeguard the confidentiality, integrity, and availability of electronic information and communication systems. This aids in the prevention of cyber dangers and vulnerabilities like as hacking, data breaches, and other cyber-attacks.Enhanced Reputation:
Compliance with NESA standards can assist businesses and organizations in developing a reputation in the UAE as a trustworthy and safe enterprise. Customers, stakeholders, and partners prefer to do business with companies that have a solid reputation for information security and compliance.Competitive Advantage:
Businesses and organizations can gain a competitive edge by complying with NESA standards. Moreover, companies that can demonstrate their commitment to security and compliance are more likely to attract customers who are increasingly aware of the importance of information security.
Types of Service we provide
- NESA Compliance Consulting
- NESA Audit
- Guidance in implementing NESA Audit
- NESA Audit Compliance Training:
- Writing and reviewing policies and procedures based on NESA IA Audit
- Writing and reviewing data handling procedures based on NESA IA Audit
- Support in reviewing, updating, or amending:
- Contracts
- Notices
- Inquiries
- Complaints
- Dispute resolution processes
NESA Audit and Compliance Process
While conducting the NESA audit, Eshield follows a Tiers-based enforcement of compliance as used by NESA. Furthermore, how regulatory agencies cooperate with you in enforcing compliance depends on the extent of risk that your organization poses to the UAE’s information infrastructure. They calculate the level of risk by considering the results of your present security controls and the inherent risk of the sector.
Stage 1
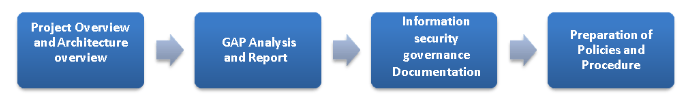
Stage 2

Related Services
Unlock the possibilities today! Eshield IT Services is among the top security companies in UAE. Explore our wide range of services and get in touch with us at Contact us or email us at [email protected] to discover how we can cater to your needs.
You can also call us at +971-585-778-145 or whatsapp
Why Eshield IT
- The NESA UAE Audit service aims to identify vulnerabilities, assess risks, and recommend robust security measures to enhance the resilience of your information infrastructure.
- Based on the findings of the NESA Audit, we provide detailed reports and actionable recommendations. These reports and recommendations enable you to make informed decisions to strengthen your security posture.
- By undergoing the NESA Audit, you demonstrate your commitment to ensuring the confidentiality, integrity, and availability of your critical information assets.
- Partner with NESA today and benefit from our expertise in securing your organization’s critical information infrastructure, aligning it with the highest standards set by the Electronic Security Authority.
- Our comprehensive NESA Audit service ensures that the Electronic Security Authority mandates your organization to meet a set of standards.
- By partnering with us, you can rest assured that your critical information infrastructure will undergo a thorough evaluation and assessment in accordance with NESA guidelines.
- Our team of experts is well-versed in the NESA framework and will assist you in achieving compliance with the established standards.


