In this article we will be diving deep about this interesting topic Red Teaming.
But before that, let us see what this Red Teaming really means !
Defining the Red Team
Red Teaming is actually a group of penetration testers who act as an attackers for attacking and gaining access to the organization with different kinds of attacking methodologies.
– The red team is encouraged to think creatively and use their own written scripts, tools for testing process.
– During the red teaming, the employees of the target organization are not aware that testing is going on.
– Red teaming members seek to discover new kind of vulnerabilities.
– Usually the red team methodologies include chaining of the attacks. Like they focus on attacking multiple domains of the target organization.
Ex: Active Directory attacks is one of such example
Now you understand what Red Teaming means.
Let us see the factors involved in red teaming engagement
Factors Involved in Red Teaming Engagement
The organization or individuals should be aware of their own systems and patch any known vulnerabilities before initiating the exercise.
Know What You Are Looking For
The organization or individuals should be aware of their own systems and patch any known vulnerabilities before initiating the exercise
Know Your Network
The better you understand your testing environment the more accurate your red team can perform with accurate results.
Know Your Budget
You should have a clear picture on how much money you can spend on the red team for the exercise. Based on that budget we set the scope for the engagement.
Know Your Risk Level
It represents the risks that actually represents the consequences for your business.
Now you understand the factors involved in the engagement process.
But before that let us see the key insight of red teaming
Key Insight of Red Teaming
> You can’t really know how secure your systems are until they are attacked
Let us now move ahead and see various types of Red Team methodologies or tactics !
Red Team Tactics
These are the most common ways that red team assessors go beyond :
– Email and phone-based social engineering :
The testers perform research on individuals and organizations. The phishing emails become a lot more convincing to attack them. This is frequently the first in a chain of composite attacks which helps to accomplish the goal.
– Network exploitation :
It aims to identify the system-level and network flaws which includes misconfigurations, daemon issues, wireless network vulnerabilities, and more.
– Physical exploitation :
It involves understanding the effectiveness and strength of physical security controls via real-life exploitation.
– Application exploitation :
It aims to identify application layer flaws such as CSRF, Injection Flaws, Weak Session Management, and the OWASP Top 10.
– All of the above :
It is an attack simulation which is designed to measure how well the networks, their applications, and their physical security controls can defend an attack from a real-life perspective.
Let us now see various tools used by red team.
Tools used by the Red Teamers
Nmap – Network Mapper
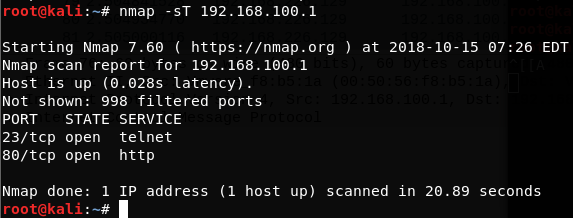
used for scanning and enumerating the services or ports on the target machine
[Nmap](https://nmap.org/) is an open source and free security tool. It was launched in 1997. It is actively maintained and it is used for detecting open ports on remote hosts, enumerating the daemons, gathering hosts, OS info, DNS info, running scripts and several other tasks that aid in red team
operations. Nmap is one of the most important tool for red teamers.
SQLmap
used for checking and exploiting the SQLi injection attacks
It is an open source penetration testing tool which launches SQL injection tests and discovers issues and vulnerabilities. The key features includes automating the code injections, enumerating the users, recognition of passwords, dictionary-based password cracking, and executing remote SQL SELECTS.
Nikto
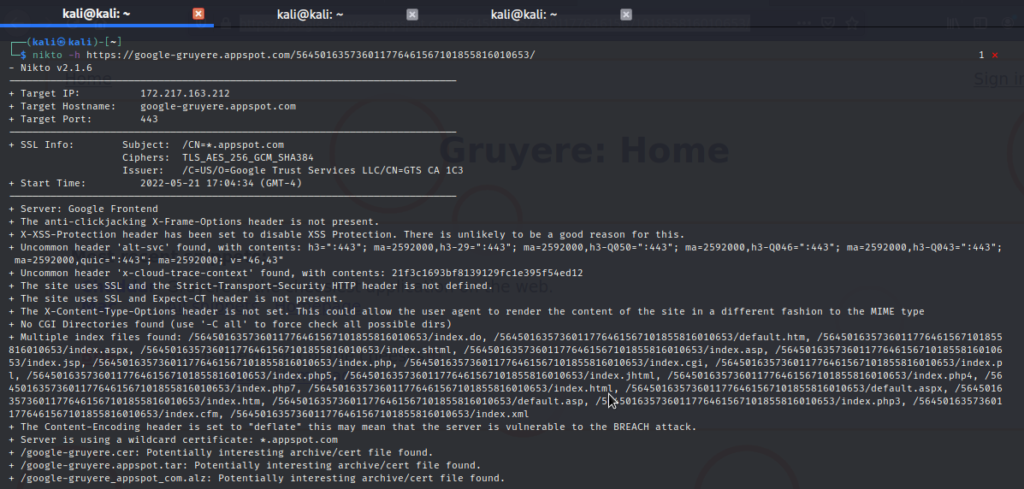
Nikto scan output assessing the vulnerabilities of a web application
It is an open source web vulnerability scanner using which you can use it to scan the web servers and discover security vulnerabilities. It is written in Perl language, it helps the red teams to detect outdated software applications and discover insecure files, and the server misconfiguration. It also features IDS evasion, XSS vulnerability tests and much more making it a perfect tool for red teaming.
OpenVAS

It is an open source network scanner used for executing the network vulnerability tests on the
target and it is used for detecting vulnerabilities. It has many attractive features, but the ones which help in red team operations include simultaneous multiple host scanning, +50k network
vulnerability checks, the scheduled scans and the false positive management.
Maltego

It is another great tool for information gathering and reconnaissance. It lets you to discover phone numbers, email addresses, names, organizations and social media accounts, and it can be used for data correlation which allows the red team to visually explore relationships in among the data.
OSINT Framework
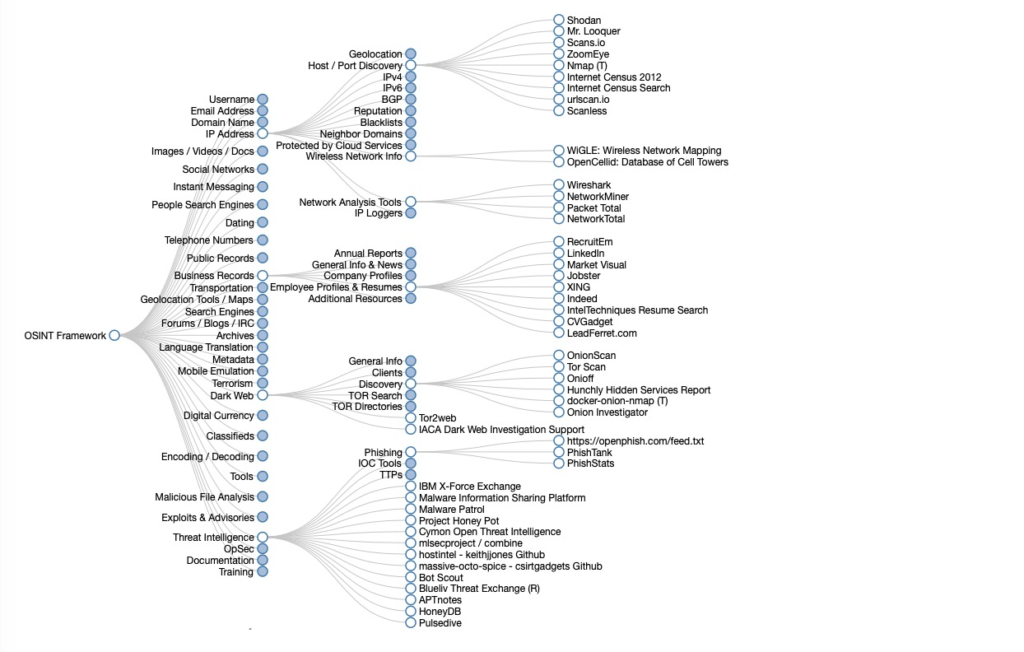
It is another one of the great information gathering tool. This framework is used for performing the reconnaissance, information gathering and OSINT research. This framework is a handy collection of OSINT tools which are filtered by categories, making red teams tasks much easier.
Shodan

It is called as ‘search engine for hackers’.It is focused on the deep web and the IoT. The IoT usually lacks proper security, and it offers multiple points of entry. It is is used to scan anything that is connected to the internet, such as routers,servers, and webcams. Shodan lets you to
scan traffic light systems, nuclear power plants, heating systems and much more.
Wireshark
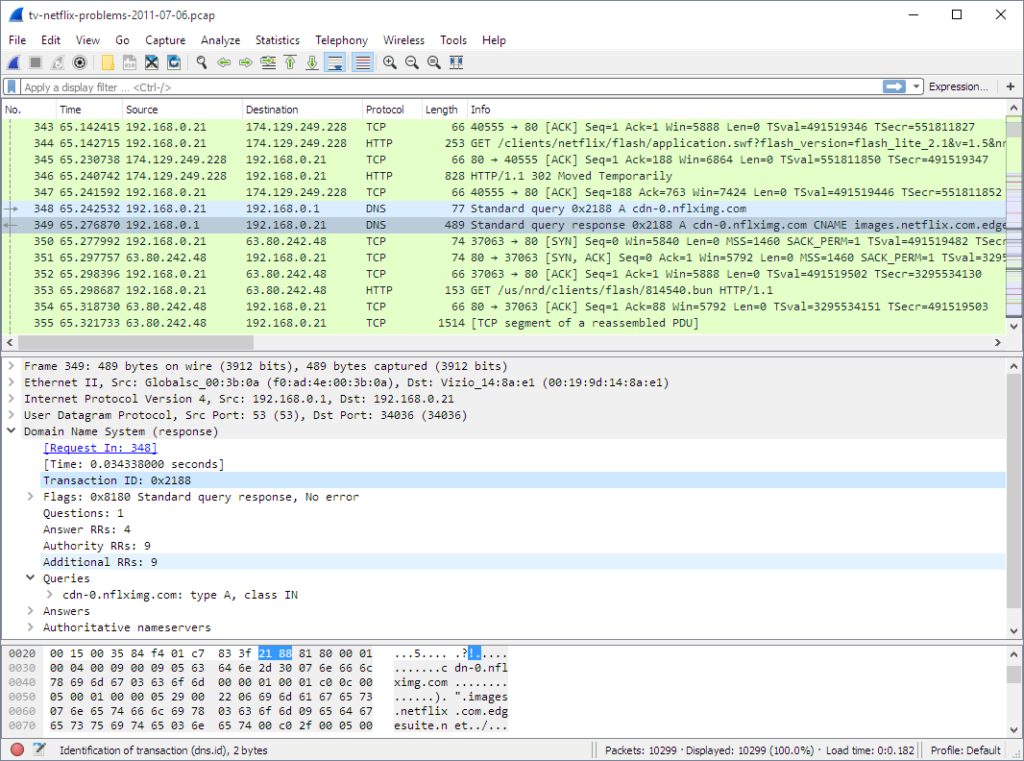
used for monitoring and analyzing the network traffic
It is an open source tool which is used for analyzing the network traffic. It helps the red teams to detect any security issues present in the target network. It analyzes the network
traffic in real time and it helps to intercept and read results. It has the capability for gathering the intelligence from various network traffic sources, the red teams can discover vulnerabilities, and threats of the target network.
Social Engineering Toolkit (SET)
SET for short it is a free open source security tool that features numerous attack techniques for performing social engineering. It includes creating a phishing page by cloning the original page, with various attack options such as spear phishing, phishing, mass
mailing, website attacks, and much more.
Metasploit
used for generating payloads and gaining access to the target
It is an open source project which offers both free and commercial versions. It is useful for many security professionals and for the red teams in discovering various security vulnerabilities and for scripting, testing and executing the exploits. The MSF version offers various capabilities for evading detection systems and runs vulnerability scans, enumerates the hosts and much more.
Gophish

It is an open source phishing framework which is highly useful for the red team
operations. It helps to create various phishing campaigns easily, schedule and launch them, it then finally tracks the results from the campaign to test an organization’s awareness of the phishing attacks.
Hashcat

It is known as the “world’s fastest password cracker.” It is an open source password hash cracker that red teams can utilize for brute forcing the passwords and performing dictionary based attacks. Hashcat is powerfull tool. It is an open source tool to consider it in your arsenal.
PowerUp
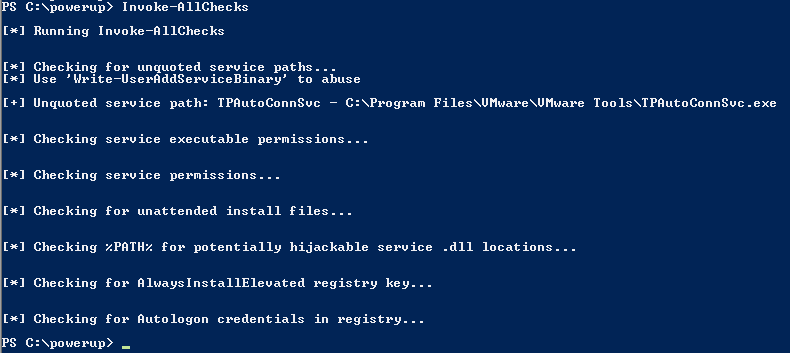
It is also called as Powershell. It is a tool which offers various checks for common misconfigurations and as well as a number of privilege attack methods for the windows, to help you with local privilege escalation on the systems. It offers various methods to abuse various services and other escalation opportunities.
Mimikatz

It is an open source tool which is considered as a staple in a red team toolkit. It is used for
extracting and collecting credential information of the windows systems from the
target. It can also perform a great functionality I.e., pass-the-hash and pass-the-ticket, rebuilds the golden tickets.
Conclusion
That’s all about the Red Team. After reading this essay, I hope you found it enjoyable and learned something new. We have learned what is Red Teaming, the factors involved, its insight, and their tactics or methodologies. Also, we learned about various tools used in red teaming.


