LockBit 3 ransomware

LockBit 3 is a type of ransomware that is designed to encrypt files on a victim’s system and demand a ransom payment in exchange for the decryption key. It is part of the LockBit ransomware family, known for its sophistication…


Security | Privacy | Compliance


Security | Privacy | Compliance

LockBit 3 is a type of ransomware that is designed to encrypt files on a victim’s system and demand a ransom payment in exchange for the decryption key. It is part of the LockBit ransomware family, known for its sophistication…
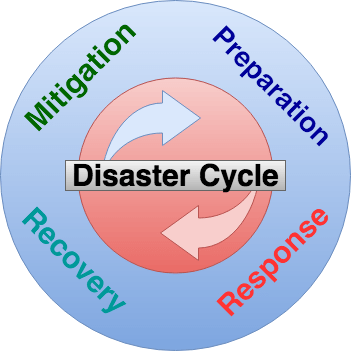
Introduction In the modern digital age, organizations are increasingly reliant on technology and data to drive their operations. However, with the rise of cyber threats, natural disasters, and human errors, it’s crucial for businesses to have a robust disaster recovery…
Introduction The importance of information security cannot be emphasised in an increasingly interconnected and digitised society. Risks to organisations include data breaches, unauthorised access, and compliance violations, all of which can have serious effects for both organisations and individuals.…

Click here to check our Cloud Security Services INTRODUCTION In recent years, Cloud computing adoption has grown tremendously, providing businesses and organisations with the flexibility, scalability, and cost-efficiency they require to prosper in today’s digital environment. However, this convenience comes…

The world of cybersecurity is always changing, and keeping up with the latest threats and vulnerabilities can be difficult. We will look at the current threat landscape and help you understand the risks you encounter when using digital devices and…

Data security is a major concern for both organisations and people. Every day, data is sent via networks and the internet in today’s digital world. This data transmission is known as data in transit, and it is subject to hacking.…

In today’s digital environment, the importance of doing regular security assessments cannot be overstated. As firms rely more and more on technology to manage their operations, sensitive data is becoming more vulnerable to cyber-attacks. These attacks can have major ramifications…

What is Cloud Computing? Setting up your business for future achievement begins with changing from on-premises equipment to the cloud for your figuring needs. The cloud gives you admittance to additional applications, further develops information openness, assists your group with…

Introduction In today’s digital age, passwords are the first line of defense against unauthorized access to personal or sensitive information. Whether it’s for email, banking, social media, or other online accounts, creating a strong password is essential. So we have…

Top 8 Cybersecurity Tips for Remote Employees Since the pandemic, remote working has become much more common worldwide. Even when the pandemic ended, working from home remained widespread across multiple sectors. While working from is helpful and has many advantages,…