
ISO 27001 Consulting service | Implementation | Certification
ISO 27001 certification is an international standard that outlines best practices for information security management systems (ISMS). It provides a framework for managing and protecting sensitive information through risk management and the implementation of security controls.
Secure your organization’s future with peace of mind and pass your ISO 27001 audit with flying colours!
ISO 27001 Compliance Guide for Business to achieve Certification
Three security objectives
There are 3 basic goals of ISO 27001:
-
Confidentiality:
only authorized persons have the right to access information.
-
Integrity:
only authorized persons can change the information.
-
Availability:
the information must be accessible to authorized persons whenever it is needed.

Benefits of ISO 27001
-
Improved Information Security:
ISO 27001 is a worldwide accepted standard outlining best practices for information security management systems (ISMS). Moreover, it creates a framework for managing and protecting sensitive information by implementing security controls and risk management.
-
Compliance with Regulations:
The standard defines the requirements for developing, deploying, maintaining, and improving an ISMS. However, this includes developing security policies, conducting risk assessments, installing security controls, and monitoring and reviewing the ISMS implementation on a regular basis.
-
Increased Efficiency:
ISO 27001 can be used by organizations to demonstrate their commitment to information security and improve their overall security posture. Certification to the standard is also becoming more relevant for businesses that deal with sensitive information or must follow legal regulations.
-
Risk Management:
ISO 27001 is a systematic and structured risk management strategy that helps enterprises to detect, investigate, and eliminate risks to their information assets.
-
Business Continuity:
By identifying and managing risks to critical information assets, ISO 27001 can help organizations ensure the continuity of business operations in the event of disruptions or disasters.
-
Cost Saving:
An ISMS certification consulting services near Dubai can help companies save money over time by lowering the cost of responding to data breaches, ensuring compliance with applicable rules and regulations, and lowering the cost of responding to data breaches.
Key Takeaways for Business:
- ISO27001 compliance is crucial for UAE businesses to secure their data and protect against potential threats.
- Implementing ISO27001 can help organizations meet information security standards.
- This guide provides easy-to-follow steps to ensure compliance and safeguard your business.
- By assessing your current data security measures, establishing a cross-functional team, and conducting risk assessments, you can enhance your information security.
- Developing policies and procedures, implementing access controls, and educating employees on information security are essential steps for compliance.
Steps in ISO 27001 Certification
-
Gap Analysis:
A gap analysis is an evaluation of an organization’s existing information security management system policy against the ISO 27001 criteria to identify areas of non-compliance and chances for development.
-
Risk assessment:
It is the process of detecting, analyzing, and evaluating threats to an organization’s information assets in order to evaluate the likelihood and effect of future security incidents.
-
Policy and Procedure Development:
Creating and documenting policies and procedures to satisfy ISO 27001 requirements can be a difficult task, but it is critical for achieving and maintaining compliance.
-
Implementation Support:
While an effective ISMS implementation can be a difficult and time-consuming process, our ISO certification consultants in UAE can give direction and help to ensure that the necessary controls are installed and integrated efficiently.
-
Internal audit:
Internal auditing of the ISMS on a regular basis can help firms uncover weaknesses and possibilities for development while also guaranteeing compliance with ISO 27001.
-
Certification:
Our team includes an ISO 27001 accredited lead auditor who can give you with ISO 27001 certification.
Our Methodology
Phase 1:
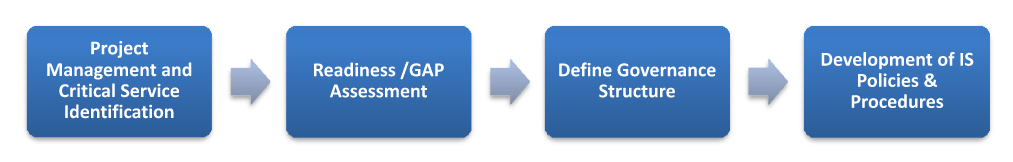
- Initially, create a project governance structure for the implementation of the project with defined project scope and deliverables
- Perform Readiness/GAP Assessment with respect to ISO 27001, IT Operation & Process, Application, End users, Supporting departments with reporting, roadmap definition & final presentation to ABC Company team
- Define Information Security Management System governance structure with documented roles and responsibility
- Development of IS policies & procedures to mitigate the identified risks.
Phase 2:
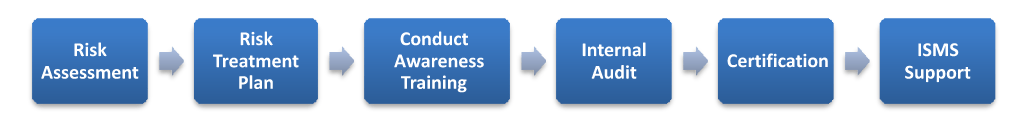
- Implement a risk management framework and identify risks posed to the organisation
- Population of risk register and updated with risk mitigation actions, and residual risks
- Selection of appropriate controls and development
- Impart training & knowledge transfer for the smooth transition of the service management & security management systems to ABC Company
- Internal audit, Corrective action – Preventive Action reports and observations
- On-going support for a period of 3 years for internal audit and external audit
Why Eshield ISO 27001 Consultants in UAE
- Value for every penny spent
- The procedure meets global standards.
- Risk strategy business enabler framework
- We prioritize service quality and customer satisfaction.
- Highly qualified and experienced team with extensive knowledge of the ISMS Standard
- Extensive practical knowledge and understanding of information security systems
Moreover, the ISO Certification in Abu Dhabi is beneficial for businesses of any size and industry, as it ensures compliance with the requirements of the Abu Dhabi information security standards Information Security Management System (ISMS) and helps in securing their information assets.
The ISO Certification in UAE is particularly relevant for industries where information protection is critical, such as financial services, banking, healthcare, public, and IT sectors. Additionally, it is mandatory for data centers and IT outsourcing companies that handle substantial volumes of data or information for clients and customers
To summarize, if you want to know more about ISO 27001 Information Security Management Certification and its prerequisites, do not hesitate to contact us. We can offer a free consultation by our best ISO certification consultants in Dubai and guide you through the certification process and implementation tailored to your organization.
ISO 27001 Certification Easy Steps
ISO 27001 Certification Process: A Step-by-Step Guide
- Understand the Standard: Familiarize yourself with the ISO 27001 standard and its requirements. Gain a comprehensive understanding of the purpose and scope of the certification.
- Gap Analysis: Conduct a thorough assessment of your organization’s current information security practices. Identify any gaps or areas of non-compliance with the ISO 27001 standard.
- Establish the ISMS: Develop an information security management system that aligns with the requirements. This involves defining policies, procedures, and controls to manage information security risks effectively.
- Risk Assessment: Perform a risk assessment to identify potential threats, vulnerabilities, and impacts on your information assets. Determine the appropriate controls to mitigate or eliminate these risks.
- Implement Controls: Implement the necessary controls identified during the risk assessment stage. These controls should address various aspects of information security, such as access control policy iso 27001, incident management, and business continuity.
- Training and Awareness: Train employees on information security best practices and their roles and responsibilities within the ISMS. Foster a culture of security awareness throughout the organization.
- Internal Audit: Conduct regular internal audits to evaluate the effectiveness of the ISMS. Identify areas for improvement and take corrective actions to address any non-conformities.
- Management Review: Engage top security information management tools in regular reviews of the ISMS. Assess the system’s performance, evaluate the effectiveness of controls, and make necessary adjustments.
- Certification Audit: Engage an accredited certification body to conduct an independent audit of your organization’s ISMS. The certification audit verifies compliance with the standard.
- Certification: Upon successful completion of the certification audit, the certification body will issue certificate, demonstrating your organization’s compliance with the standard.
FAQ
What is ISO27001 compliance?
ISO27001 compliance refers to following the information security standards set by ISO27001. It involves implementing measures to secure data and protect organizations from potential threats.
Why is ISO27001 certification important for businesses?
ISO27001 certification is crucial for businesses as it demonstrates their commitment to information security. It helps build trust with stakeholders and ensures compliance with industry standards.
How do I assess my current data security measures?
To assess your current data security measures, conduct a thorough evaluation to identify vulnerabilities and areas for improvement. This assessment will provide insights into the strengths and weaknesses of your security infrastructure.
How can I establish a cross-functional team for ISO27001 compliance?
To establish a cross-functional team, gather representatives from IT, legal, HR, and other relevant departments. This team will work together to develop and implement comprehensive information security protocols.
What is the process for conducting a risk assessment?
Conducting a risk assessment involves identifying and assessing potential risks to your organization’s information security. This process helps prioritize efforts and develop effective risk mitigation strategies.
How do I develop information security policies and procedures?
Developing information security policies and procedures involves creating a comprehensive framework that aligns with ISO27001 standards. These policies provide guidelines for safeguarding data and establishing security protocols.
What are access controls and how do I implement them?
Access controls refer to measures that control access to sensitive information. Implementing access controls involves establishing protocols for user management, securing privileged access, and monitoring access activities.
How can I educate my employees on information security?
Educating employees on information security involves developing an effective security awareness program. This program ensures that employees are well-informed about their responsibilities in maintaining information security.
Why are regular security audits important for ISO27001 compliance?
Regular security audits are essential for maintaining ISO27001 compliance. These audits help identify any non-compliance issues and ensure that your organization’s information security practices are up to date.
What is incident response and business continuity planning?
Incident response and business continuity planning involve developing plans to address security incidents and minimize disruptions to business operations. These plans ensure that your organization can effectively respond to and recover from security incidents.
How can I ensure third-party compliance with ISO27001 standards?
Ensuring third-party compliance involves assessing and monitoring vendors to ensure they meet ISO27001 standards. It includes conducting vendor assessments and implementing ongoing monitoring protocols.
Why is continual improvement and training important for ISO27001 compliance?
Continual improvement and training programs are crucial for maintaining ISO27001 compliance. They ensure that your organization stays updated with evolving information security practices and continually enhances its security measures.
What security measures should I implement for remote work?
Implementing security measures for remote work involves addressing the unique security challenges presented by remote work scenarios. These measures include secure remote access, encrypted communication, and employee training on remote security best practices.
How can I monitor and report on ISO27001 compliance?
Monitoring and reporting on ISO27001 compliance involve utilizing tools and processes to track compliance, address non-compliance issues, and generate accurate reports for stakeholders. This ensures ongoing compliance and transparency.
Conclusion
In conclusion, this ISO27001 compliance guide has provided you with a comprehensive overview of the steps required to ensure your UAE business meets information security standards. Implementing ISO27001 is crucial for securing your data and protecting your organization from potential cyber threats. By following the guidance and best practices outlined in this guide, you can confidently establish a robust information security framework.
Remember, ISO27001 compliance is an ongoing process that requires continual improvement and vigilance. Regularly assess your data security measures, establish a cross-functional team, and conduct risk assessments to stay ahead of evolving threats.
Education and awareness among employees are key to maintaining a strong security culture. Develop comprehensive information security policies, implement access controls, and regularly conduct security audits to ensure ongoing compliance. Additionally, prioritize incident response and business continuity planning, and carefully manage third-party vendor compliance.
By adhering to these steps and implementing ISO27001 standards, you can safeguard your organization’s sensitive information and create a secure environment for your business to thrive in the UAE.

