Top 8 Cybersecurity Tips for Remote Employees
Since the pandemic, remote working has become much more common worldwide. Even when the pandemic ended, working from home remained widespread across multiple sectors.
While working from is helpful and has many advantages, it likewise uncovered the two people and organizations to a scope of cybersecurity threats. That is why it is fundamental to consider home cybersecurity seriously. By following best practices, you can reduce most cybersecurity risks that come while working from home.
How to stay safe during work from home?
With the ascent of remote working, cybersecurity threats- specifically, phishing – have become more common. The main issue is that, in many work environments, an IT group will deal with network safety inside the workplace. But, with employees working from a distance, staff need to focus harder on cybersecurity attacks themselves. Here are the top remote working security tips to guarantee you and your staff are telecommuting securely.
Cybersecurity while working from home is more dependent upon you, while another person ordinarily deals with it at the office. Regardless of whether you are utilizing a laptop given by your manager, there actually are measures that are left to you.
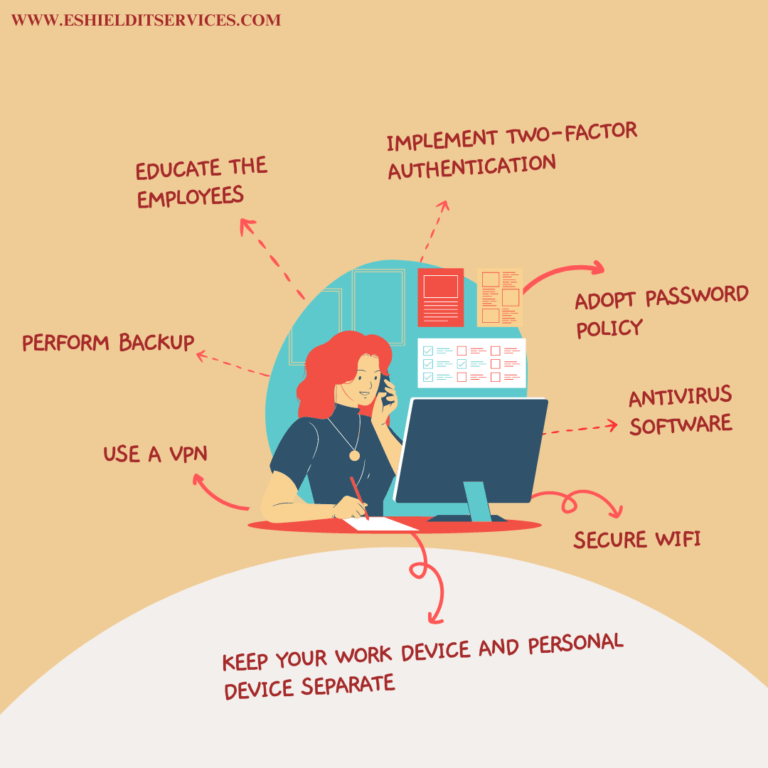
Here are the top 8 cybersecurity tips for remote workers: –
1. Educate the employees
It is very important for the employees to understand why cybersecurity is important in order to know what is at stake. There has been a 400% hike in cyberattacks since the beginning of the pandemic, and the risk surely isn’t disappearing.
If a company loses customer data due to a cyberattack, it can result in financial loss and reputational loss. Basically, in the event that the organization struggles with any kind of loss it could lead to the loss of jobs.
That’s why HR departments must be proactive about data security and enroll employees in staff awareness training classes as soon as they are hired.
2. Perform backup
You will very likely have countless digital documents on your computer system that must be protected, these documents include invoices, contracts, employee files, and non-disclosure agreements.
In case the files are lost it is important for you to have backup copies on a separate server so that you can access the information in the event that the original documents are compromised.
3. Adopt password policy
To avoid any security breaches, it is important to have a strong password. There should be a set of rules implemented by the IT department to create strong password creation and management.
Passwords must be unique, avoiding obvious themes such as a pet’s name or favorite sports team. Cybersecurity experts also often recommend a combination of at least 8 letters, numbers, and special characters.
4. Antivirus software
Cyber attackers introduce viruses to your security system and try to steal data. Companies must install antivirus software to reduce this risk. Antivirus software alerts the users when the system is contaminated by malicious files and prevents intrusions at the source. Antivirus suites take the hard work off your hands by offering automatic remote work security against a host of threats, including:
● Zero-day attacks
● Malware, spyware, and viruses
● Trojans and worms
● Phishing scams
5. Keep your work device and personal device separate
It’s a significant safety effort to keep your work gadgets and individual devices separate. While it might be helpful to sign onto a work account on your phone or laptop or sign in to your social media accounts on your work computer, this isn’t suggested. If your device has a security breach, you don’t want a hacker to get confidential information. Keeping each of your devices separate assists with limiting how much sensitive information a cyber attacker can get their hands on.
This action additionally assists with keeping your everyday life separate from your professional life. If you use a common gadget for work that your family has access to, this might possibly lead to security breaches. For example, a relative could unintentionally install a malicious application, access the organization’s information, or in any case, meddle in your work life. Having a secure, separate device is the least demanding method for drawing limits between these two parts of your life. If you have had any desire to take this a step further, you can likewise lay out a home security network for your family’s devices and filter out possibly unsafe sites or applications.
6. Secure Wi-Fi
Ensuring your Wi-Fi is secure is a significant network protection way to work from home. By penetrating your Wi-Fi organization, programmers might possibly get close enough for your gadgets, or utilize your Wi-Fi network for a crime. As an initial step, you’ll need to change the default password for your Wi-Fi router to a new password.
Other things you can do to keep your wireless network secure include implementing encryption and ensuring you remain up-to-date with recent security updates. Although it could be tempting to use public Wi-Fi at a cafe or local park, it is not advised to take a risk. Public Wi-Fi is more vulnerable to threats, so it is better to use a private network that is more secure.
7. Use a VPN
VPN security can be upgraded by utilizing the heartiest conceivable confirmation technique. Numerous VPNs use a username and password; however, you might need to move up to the usage of smart cards. You can likewise improve your encryption strategy for VPN access, for instance, by overhauling from a Point-to-point Tunneling to a Layer Two Tunnelling Protocol (L2TP). It is necessary for employees to update their passwords consistently. Employees should only use the VPN when they really need to and switch it off when they are using their work devices for personal use.
8. Implement two-factor authentication
Up until recently, having a strong and unique password was the only way to secure an account. But now with the advancement of technology and with the ways of cyber attackers evolving with the technology, adding a second layer of security with two-factor authentication protects the employees if their password is compromised. Multi-factored authentication expects people to provide a password to enter a second piece. This can be a code, one-time password, fingerprint or face scan.
Please visit our Services page for a full range of services offered.


