
Best practices for securing web applications
Introduction With the growing reliance on web applications for a variety of functions, it is…


Security | Privacy | Compliance


Security | Privacy | Compliance

Introduction With the growing reliance on web applications for a variety of functions, it is…
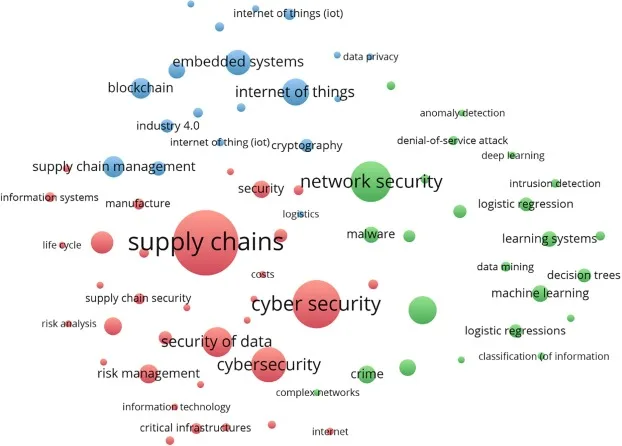
Introduction Supply chain management relies on cybersecurity to secure the integrity, confidentiality, and availability of…

Introduction A new threat is emerging in the world of cybersecurity that is capable of…

Introduction In the modern age, protecting sensitive data has become a serious issue for businesses…