2024 RoadMap: How to Become a Cloud Security Engineer

What is the Career Outlook for Cloud Security Engineers in 2024? How to Start a Career as a Cloud Security Engineer?

Security | Privacy | Compliance

Security | Privacy | Compliance

What is the Career Outlook for Cloud Security Engineers in 2024? How to Start a Career as a Cloud Security Engineer?

Honeypots are one of the most essential tools in modern cybersecurity defenses. They are designed to attract and detect cyberattacks, allowing network administrators to gain valuable insights into the tactics and techniques used by hackers. In this article, I will…
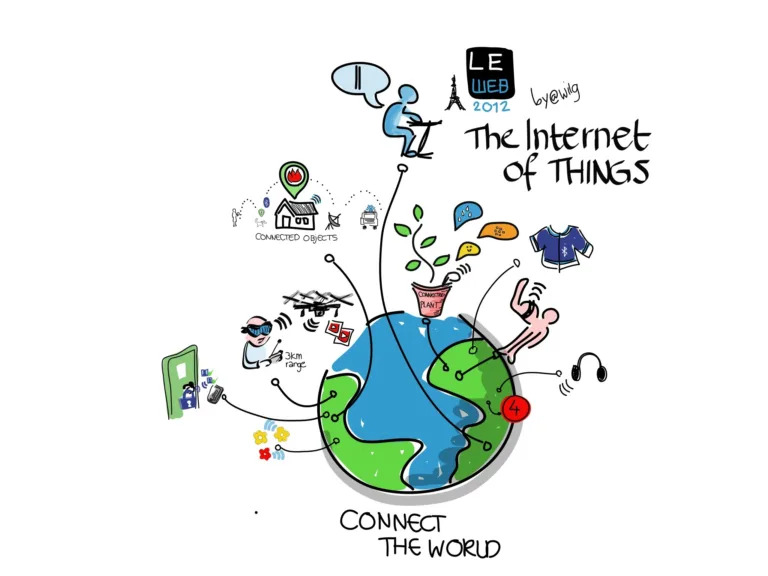
INTRODUCTION The Internet of Things (IoT) has changed the way people interact with technology by connecting devices and allowing them to communicate and exchange data. While IoT offers several benefits and convenience, it also poses security concerns. Security of IoT…

The world of cybersecurity is always changing, and keeping up with the latest threats and vulnerabilities can be difficult. We will look at the current threat landscape and help you understand the risks you encounter when using digital devices and…

Data security is a major concern for both organisations and people. Every day, data is sent via networks and the internet in today’s digital world. This data transmission is known as data in transit, and it is subject to hacking.…

What is Cloud Computing? Setting up your business for future achievement begins with changing from on-premises equipment to the cloud for your figuring needs. The cloud gives you admittance to additional applications, further develops information openness, assists your group with…
Introduction The metasploit is a computer security project that provides information about security like vulnerability and penetration testing. It is most widely used in vulnerability scanning and exploitation. The metasploit framework is the most potent tool that cyber criminals and…
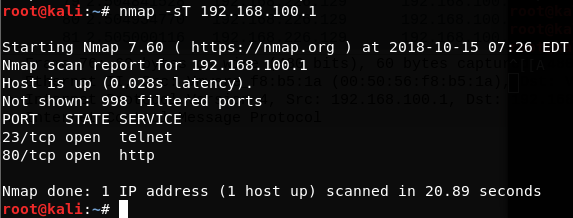
In this article we will be diving deep about this interesting topic Vulnerability Assessment & Penetration Testing (VAPT).But before that, let us breakdown VAPT and see what it really means !Let us now understand what a vulnerability means. Vulnerability It…
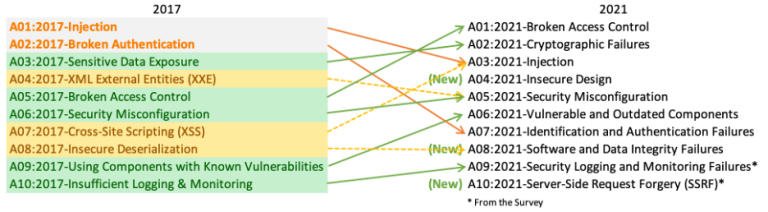
In this article we will be diving deep about this interesting topic Web Application Audit. But before that, let us see what this Web Application Audit really means ! Defining the Web Application Audit The auditing looks for the security…

In this article we will be diving deep about this interesting topic Protecting from Ransomware Attacks. Now, let us see what it means ! Introduction – What precisely is ransomware? – Infection with ransomware indicates that your operating system…