What is Defense in Depth and How Does it Work?

Understanding the Concept of Defense in Depth
Defense in depth is a cybersecurity strategy that involves implementing multiple layers of security measures to protect an organization’s critical assets. The idea behind defense in depth is that no single security measure is foolproof, so by layering multiple defenses, an organization can better protect itself against cyber attacks.

1. Layered security:
This involves implementing multiple layers of security controls, such as firewalls, intrusion detection systems, access controls, and encryption, to create a more robust defense system.
2. Redundancy:
By having redundant security measures in place, organizations can ensure that if one layer of defense fails, there are still other layers of protection in place to prevent a security breach.


3. Defense at multiple points:
Defense in depth involves protecting critical assets at multiple points in the network, such as at the perimeter, within the network, and at the endpoint level, to mitigate the risk of a successful cyber attack.
4. Defense against different types of threats:
A defense in depth strategy should address a wide range of potential threats, including malware, phishing attacks, insider threats, and DDoS attacks, to provide comprehensive protection for the organization’s assets

How Does Secrets Management Enhance Cybersecurity?
Secrets management enhances cybersecurity by ensuring that sensitive information, such as passwords, API keys, and encryption keys, is securely stored, accessed, and used by authorized users only. By effectively managing secrets, organizations can prevent unauthorized access to critical systems and data, reduce the risk of data breaches and cyber attacks, and maintain compliance with industry regulations.

1. Securely store and distribute secrets:
Secrets management solutions encrypt and securely store sensitive information in centralized repositories, ensuring that data is protected both at rest and in transit. This helps to prevent unauthorized access and misuse of sensitive information.
2. Control access to secrets:
Secrets management tools allow organizations to define and enforce access controls, ensuring that only authorized users and applications can retrieve and use secrets. This helps to prevent insider threats and unauthorized access to critical systems.


3. Rotate and expire secrets:
Secrets management solutions automate the process of regularly rotating and expiring secrets, such as passwords and encryption keys, to reduce the risk of unauthorized access. This helps to prevent attackers from using compromised secrets to gain access to systems and data.
4. Monitor and audit secret usage:
Secrets management tools provide visibility into how and when secrets are used, allowing organizations to monitor for suspicious activity and enforce compliance with security policies. This helps to detect and respond to potential security incidents in a timely manner.

Utilizing Multiple Layers of Defense for Effective Detection
In order to effectively detect and prevent security breaches, organizations should implement multiple layers of defense. This approach, known as defense in depth, ensures that if one layer is breached, there are additional layers to protect against further attacks.

1. Network Layer:
A robust firewall and intrusion detection system can help monitor and block suspicious incoming and outgoing traffic. Network monitoring tools can also help detect unusual patterns that may indicate a potential breach.
2. Endpoint Layer:
Antivirus software, endpoint detection and response (EDR) solutions, and mobile device management tools can help protect individual devices from malware and other threats. Behavioral analysis tools can also help identify unusual activity on endpoints.
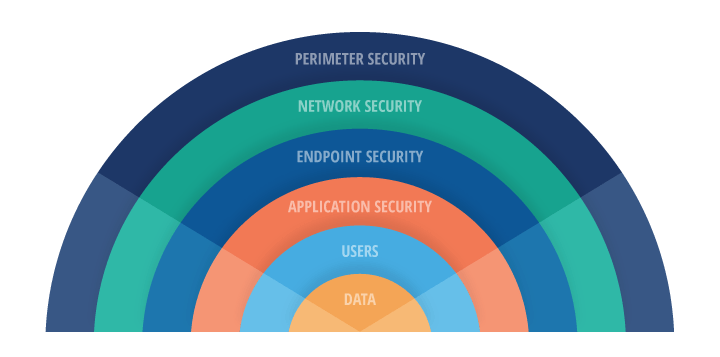

3. Application Layer:
Web application firewalls and application security testing tools can help detect and prevent attacks targeting specific applications and services. Secure coding practices and regular application security assessments are also essential for maintaining the security of applications.
4. Data Layer:
Data loss prevention (DLP) tools can help monitor and protect sensitive data from unauthorized access and exfiltration. Encryption and access controls can also help ensure that data is only accessed by authorized users.


5. User Layer:
Security awareness training can help educate employees about common threats and best practices for staying secure online. User behavior analytics tools can also help detect unusual user activity that may indicate a compromised account.
Our Services
such as network security, endpoint security, cloud security, web application security, data protection, and security compliance. Our team of highly skilled and experienced professionals work tirelessly to protect your business from cyber threats and ensure the confidentiality, integrity, and availability of your sensitive information. Whether you are a small business or a large enterprise, we have the expertise and tools to safeguard your digital assets and keep your operations running smoothly. Contact us today to learn more about our comprehensive cyber security services.

Frequently Asked Questions
1. What is Defense in Depth?
Defense in depth is a security strategy where multiple layers of security measures are implemented to protect systems and data from various cyber threats.
2. How does Endpoint Security contribute to Defense in Depth?
Endpoint security focuses on securing individual endpoints like computers, smartphones, and servers, which is one layer of defense in a comprehensive defense-in-depth strategy.
3. What role does Secrets Management play in Cybersecurity?
Secrets management involves the secure storage and management solutions of credentials and other sensitive information to prevent unauthorized access and data breaches.
4. Why is Detection an essential part of Defense in Depth?
Cyber detection mechanisms help identify and mitigate threats like malware and intrusions across different layers of defense.
5. How can Endpoint Privilege Management enhance Security?
Endpoint privilege management restricts access rights based on least privilege principles, strengthening endpoint security and overall cybersecurity posture.
6. What are the benefits of Implementing Defense-in-Depth Strategies?
Implementing defense-in-depth strategies provides multiple layers of defense that enhance security controls and help secure networks from malicious activities.
7. How does Incident Response fit within Defense in Depth?
Incident response is a crucial part of cybersecurity that involves preparing for, responding to, and recovering from security breaches across various layers of defense.
Discover the impenetrable shield of cybersecurity for your business. Partner with Eshield IT Services today to fortify your defenses. Reach out to us at Contact us or via email at [email protected]. Direct inquiries and consultations can be made at +971-487-441-45 or through WhatsApp. Safeguard your business while unlocking its true potential