In this article we will be diving deep about this interesting topic Vulnerability Assessment & Penetration Testing (VAPT).
But before that, let us breakdown VAPT and see what it really means !
Let us now understand what a vulnerability means.
Vulnerability
It is defined as the state of being exposed to the possibility of being attacked or harmed.
Now, you understand what a vulnerability means. Let us see what does vulnerability assessment (VA) mean !
Vulnerability Assessment (VA)
Vulnerabilities in computer systems, applications, and network infrastructure are defined, identified, classified, and prioritized through this procedure. Systematic approach to find the security loopholes in a network or software system.
- Process of finding vulnerabilities, with the objective that none of the loopholes are missed
- It lists the vulnerabilities during the assessment process based on the severity and criticality of the business logic
- A non-intrusive process and can be done without threatening the IT infrastructure or application’s operations
Let us see the types of Vulnerability Assessments.
Types of Vulnerability Assessment
1. Active Assessment
2. Passive Assessment
3. Host-based Assessment
4. Internal Assessment
5. External Assessment
6. Network Assessment
7. Wireless Network Assessment
8. Application Assessment
Outcomes of Vulnerability Assessment
The outcome of a VA process is an assessment report listing all vulnerabilities, categorized based on their severity.
This report servers as a base for Penetration Testing (PT). Now you go to know the outcomes of VA. Let us learn about Penetration Testing or pentesting (PT).
Penetration Testing (PT)
It is the process of hacking a system with the permission from the owner of that system, to evaluate security, Hack Value, attacks, exploits, zero-day vulnerability & other components such as threats, vulnerabilities, and daisy chaining.
- A goal oriented exercise
- Find exploitable flaws and measure the severity of each
- It tries to exploit the vulnerabilities which helps to determine
- If there is any unauthorized access or if any probability is there to perform any malicious activity
- To identify which flaws poses the threat(s) to the application
- Show how damaging a flaw could be in a real attack rather than listing every flaw
- More focused on simulating a real-life attack, testing defenses and mapping-out paths a real hacker could take
- Involves the use of automated vulnerability scanners and other manual pen-test tools
Let us see the types of penetration testing methodologies.
Types of Penetration Testing
White Box
This is a type of pentesting in which the pentester has the complete knowledge of computer system and the information of the target.
Black Box
This is a type of pentesting in which the pentester performs blind testing which means the attacker performs attacks with no prior knowledge of the system.
Gray Box
This is a type of pentesting in which the pentester has very limited prior knowledge of the system or information relevant to the targets such as IP address.
Let us look into the phases of penetration testing process.
Phases of Penetration Testing
1. Pre-Attack Phase : It focuses on the planning and preparation of the penetration test, it is done prior to any direct engagements to the target system or network.
2. Attack Phase : It uses the web application attacks, such as XSS, SQLi and backdoors, to uncover a target’s vulnerabilities.
3. Post-Attack Phase : In this phase, the pentester submits a detailed report on all the findings and solutions to eliminate the potential threats.
Steps of Penetration Testing Process
Penetration Testing Process
- Reconnaissance
The first step in pentesting, where information about the target is gathered using OSINT tools. Example: Collecting employee data or mapping network topologies. - Scanning
In this phase, testers use tools to identify open ports, services, and monitor network traffic to find potential entry points. - Gaining System Access
The tester exploits vulnerabilities to access the target system and escalates privileges to gain deeper control. - Persistent Access
The goal here is to maintain long-term access and control over the system, often by gaining high-level privileges. - Analysis and Reporting
The final step involves documenting the vulnerabilities found, tools used, and suggesting preventive measures to strengthen security.
Outcome of Penetration Testing (PT):
A detailed understanding of security weaknesses, their potential impact, and steps to mitigate them, helping organizations improve their cybersecurity posture.
Outcome of Penetration Testing
The outcome of a Penetration Testing is, generally, a evidence in the form of a screenshot or log, which substantiates the finding and can be a useful aid towards remediation.
Let us now distinguish Vulnerability Assessment and Penetration Testing !
Vulnerability Assessment (VA) Vs Penetration Testing (PT)
-Vulnerability Assessment is a list-oriented approach while PT is goal-oriented
– Penetration Testing is more useful when the target’s security maturity level is high / defense is strong
– Penetration Testing is an effective approach with specific goals in mind
– PT is most suitable in situations where depth over breadth is preferred
– VA is more useful in situations
– where there are known security issues
– when a low-maturity organization would like to get started
– VA is most suitable in situations where breadth over depth is preferred.
Let us finally discuss about tools used in Vulnerability Assessment and Penetration Testing !
Tools used in Vulnerability Assessment (VA)
Nikto
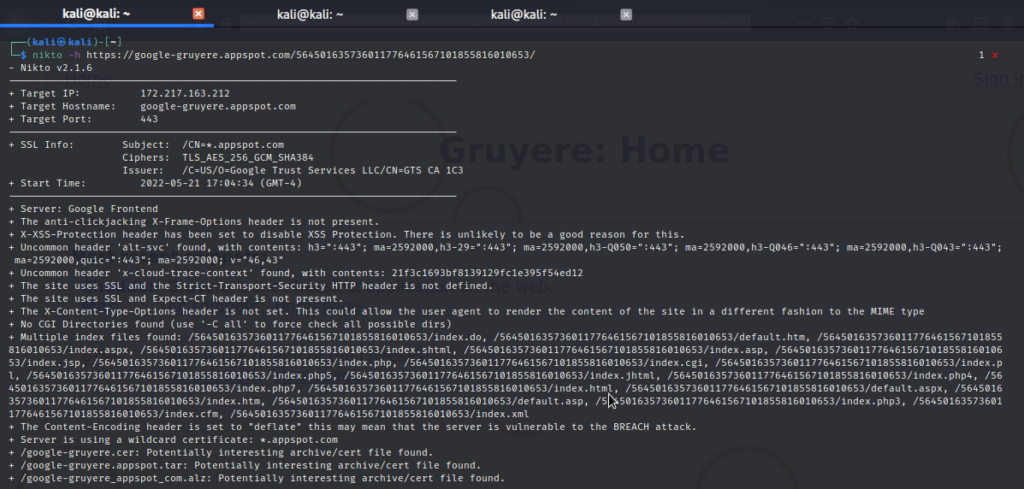
Nikto scan output assessing the vulnerabilities of a web application
BurpSuite

used for intercepting, intruding, repeating the web requests between client and server
Nessus (https://
used for assessing the vulnerabilities
Acunetix(https://
used for assessing the vulnerabilities
OWASP ZAP(https://

used for assessing the vulnerabilities
OpenVas (https://

Tools used in Penetration Testing (PT)
Wireshark
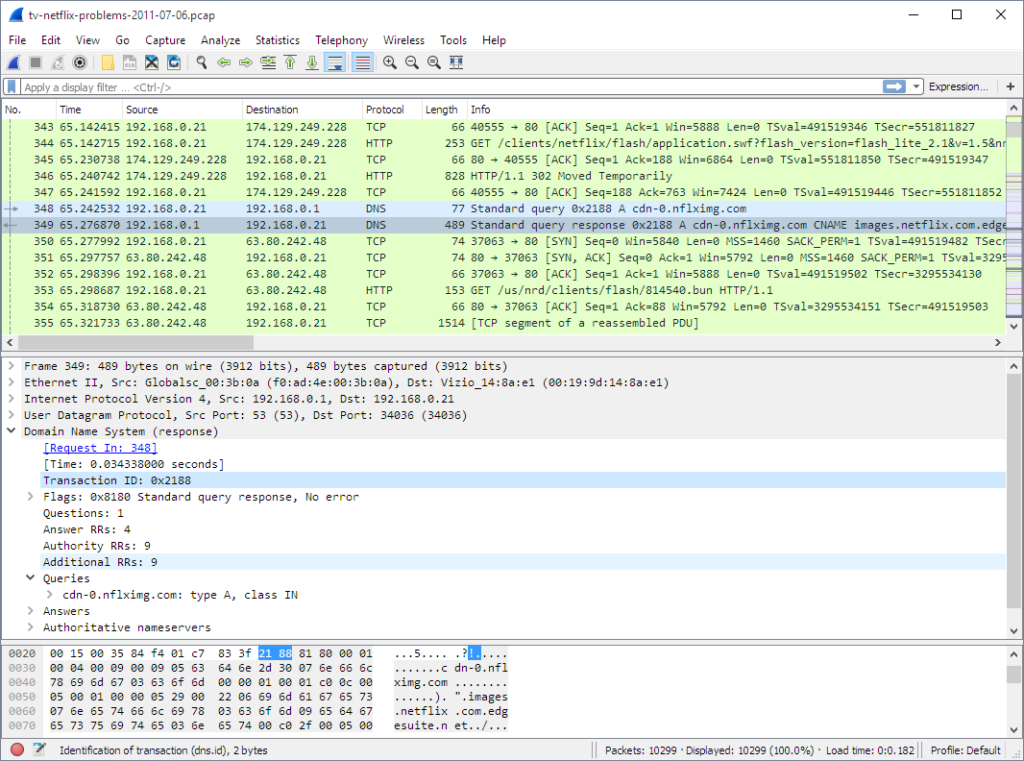
used for monitoring and analyzing the network traffic
Nmap – Network Mapper
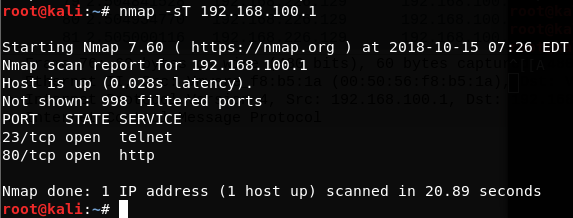
used for scanning and enumerating the services or ports on the target machine
Metasploit
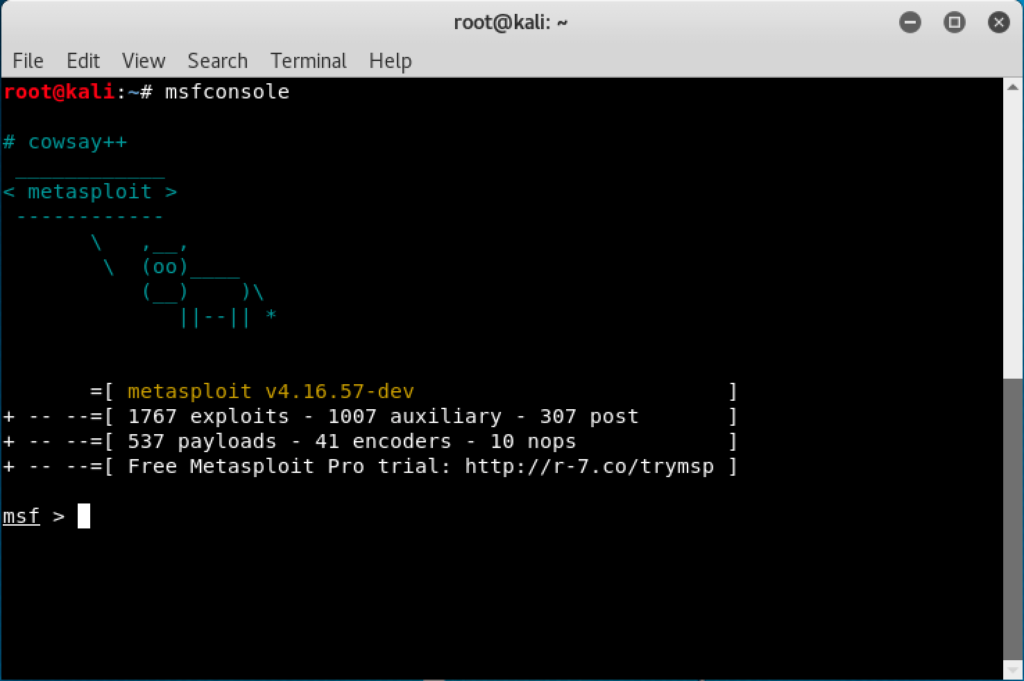
used for generating payloads and gaining access to the target
Aircrack-ng

used for wireless pentesting process
SQLmap
used for checking and exploiting the SQLi injection attacks
JohnTheRipper

used for cracking the passwords
Conclusion
That’s all about the Vulnerability Assessment and Penetration Testing.
We have learned what is vulnerability assessment (VA), its types, outcomes of it, tools and their uses. Also, we have learned about penetration testing (PT), phases of it, types of it, steps, outcomes of it, tools and their uses. We also distinguished between VA & PT.
After reading you have understanding about Vulnerability Assesment and Penetration Testing. Once can look into these tools and plan the assesment.
Please not dont use these tools untill you are sure about the environment.

