In this article we will be diving deep about this interesting topic Top SIEM Solutions.
Now, let us see what it means !
SIEM
– Log management and thorough security depend heavily on SIEM systems. Here is a list of the top SIEM tools available for firms wishing to expand or enhance their systems.
– Through features like log management and security information management, security information and event management, or SIEM, offers insights into a business IT environment. The complete security capabilities that the best SIEM software can provide are advantageous to almost all businesses. Look for features like compliance reporting, threat detection, historical log analysis, a user-friendly dashboard, and advanced analytics capabilities when selecting a SIEM product.
– I go over a number of the top SIEM products available today to assist you in selecting the finest SIEM solutions for your company. I start with my top choices, SolarWinds Security Event Manager and Threat Monitor, which strike a balance between price and feature-richness. For excellent log management and robust security, check out these. Beyond these, the market is crowded, so I’m here to provide the fundamentals of what you need know about a variety of the top SIEM products. Here are my recommendations for the best SIEM products in light of that.
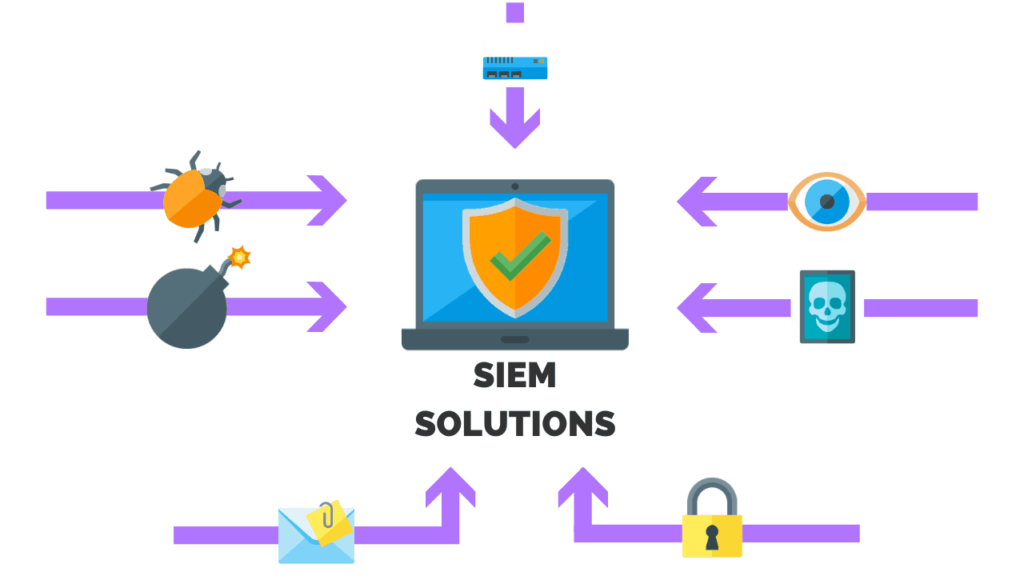
What Is Security Event and Information Management?
– A SIEM system is the greatest approach to develop an efficient cybersecurity protocol for your firm. The best option for businesses to safeguard sensitive data is through Security Information and Event Management (SIEM) systems, which have been available for more than a decade. Small and mid-sized organizations (SMBs) can still benefit from SIEM capabilities, generally through a relationship with a managed service provider. Larger enterprises are the main users of SIEM products as they are more likely to need IT oversight (MSP).
– A SIEM product might describe individual capabilities like log management, security log and event management, security event correlation, and security information management. Not every SIEM tool covers every function. Businesses are also picking SIEM products more frequently because they may assist in coordinating their security approach with particular compliance frameworks. The majority of these functions—or all of them—are frequently combined into a single product for commercial usage, albeit there is no assurance that all of the features are equally optimized.
– In essence, log data collection and aggregation is how SIEM products work. A SIEM system analyses security warnings from a variety of hardware and software across a network, including firewalls, servers, and antivirus software. Only a SIEM tool can provide you with a “big picture” understanding of your cybersecurity threat landscape; these more specialised solutions are insufficient on their own to safeguard a company. SIEMs are able to identify and counteract live threats, but they can also examine logs for information on attacks and anomalies that have already occurred, providing you with the “why” of an occurrence.
– Since it has proven indisputably useful to be able to gather information and threats from throughout your IT system onto a single, user-friendly dashboard, SIEM products are proving to be more crucial than ever. Additionally, a lot of the intelligent technologies available today are set up to automatically detect suspicious patterns and, in some cases, help tackle the underlying problem. The finest SIEM tools can distinguish between genuine threats and legitimate use using historical trends, helping you reduce false alarms while yet maintaining maximum protection. In the end, there’s really no excuse for using a subpar tool when there are so many effective alternatives that are readily accessible.
The Best SIEM Solutions: What to Look for
– A few fundamental traits define SIEM products. They take information from various sources (including threat intelligence), evaluate it, deliver warnings, run analytics, and offer a summary or historical perspective. Each company will undoubtedly have its own standards for determining whether a tool’s capabilities meet their demands when selecting a SIEM security solution. This will depend on elements like business size, data types, vendor pool, particular regulatory frameworks, budget, and, of course, usability preferences of an IT team. As you investigate the top SIEM tools available, there are a few inquiries you should make.
– Will the tool genuinely help you become a better log collector? This is elementary but crucial since you want software that makes gathering and managing logs easier. Consider system and device compatibility, and a dashboard with user-friendly features is always a plus.
– Can you achieve compliance using the tool? Find a tool that facilitates reporting and auditing. Even if you don’t worry about compliance right now, you should. Use a SIEM tool to improve your performance in this area.
– Are you able to manage previous security occurrences with the help of the threat response workflow? One of the key benefits of a SIEM tool is that it enables you to gain an overview of previous events, assess what transpired, and teach the system to apply historical patterns to guide its future behavior. Analytical drill-down capabilities are something to look for.
– Does the tool offer the automatic, quick responses you require? First and foremost, a quick event response time is essential. Customizable security alarms can also significantly simplify your life. You want to be able to walk away without worrying that you’re ignoring a significant problem. Make sure the tool prioritizes alerting.
SolarWinds SIEM Security and Monitoring
– Best for Small, Medium, and Large businesses.
– SolarWinds offers a free 30-day trial that is completely functional. The price starts at $4665. It will cost you a one-time fee.
– Through Log and Event Manager, SolarWinds offers a solution for on-premises network threat detection. It offers capabilities for automated threat remediation and USB device monitoring. New features in the Log and Event Manager include log filtering, node management, log forwarding, the Events panel, and a higher storage cap.
– Features :
– It has forensic analysis and powerful search capabilities.
– Threats will be identified more quickly with event-time detection of questionable activities.
– It is prepared for regulatory compliance. It supports HIPAA, PCI, DSS, SOX, DISA, STIG, and other regulations for this.
– It keeps up ongoing security.
– Windows, Linux, Mac, and Solaris can all run SolarWinds. Reviews indicate that while SolarWinds lacks a comprehensive security suite, it nevertheless has useful features and capabilities for threat detection.
Datadog
– Through real-time threat detection, Datadog Security Monitoring aids in the security of your tech stack. Key security integrations can be set up quickly, OOTB detection rules may be used without a query language, and security signals can be correlated to look into shady activities.
– The development, operations, and security teams are all integrated onto a single platform using Datadog Security Monitoring. Devops content, business KPIs, and security content are all displayed on a single dashboard. Real-time threat detection and security alert investigation spanning infrastructure measurements, distributed traces, and logs.
– Key characteristics :
– Datadog Security Monitoring allows you to get metrics, logs, and traces from your whole stack in addition to your security products thanks to its more than 450+ vendor-backed connectors.
– You may use Datadog’s Detection Rules to quickly and effectively identify security risks and unusual activity in any ingested logs.
– With default out-of-the-box rules for common attacker approaches, you can start identifying threats in only a few minutes.
– No query language is necessary; simply change and customise any rule using our straightforward rules editor to match the unique demands of your company.
– With Datadog Security Monitoring, you can eliminate silos between the development, security, and operations teams.
Conclusion
That’s all about the SIEM Solutions. After reading this essay, I hope you found it enjoyable and learned something new. We have learned about what to look for the best in SIEM solutions and software’s relevant to them.