


Penetration Testing In UAE
Penetration Testing, also known as “pen testing”, is a simulated cyber attack performed on a computer system, network, or web application to evaluate its security. The goal of a penetration test is to identify vulnerabilities and weaknesses in the system and to assess the effectiveness of security controls in place. Penetration testing is a proactive approach to improving cybersecurity by providing organizations with a clear understanding of their security posture and the risk of a potential attack.
Penetration Testing Service in UAE can be performed using manual testing methods or automated tools, and can be done on-demand or on a regular basis to assess the effectiveness of security controls over time. The results of a penetration test can be used to develop and implement security improvements, to enhance security awareness, and to assess compliance with industry standards and regulations.
Our Services

Firewall, IDS & IPS
Network & Infrastructure

Server & Endpoint
IoT Devices
Your Key Benefits

Assessment Report
Our experts after performing the task will you provide a detailed assessment report which will be beneficial in understanding the flaws in your company.
![]()
Security Certificate
We will help to get certified with your personal choice certification.

Expert Consultants
We also make sure you that your assessments are performed by qualified experts which have certificates like CEH, OSCP, CISA, CISSP .
Our Penetration Testing Methdology
We take holistic approach to perform penetration test with security checklists based on industry standards, including OWASP Top Ten, PCI Compliance etc., combined with our experts to yield best results.
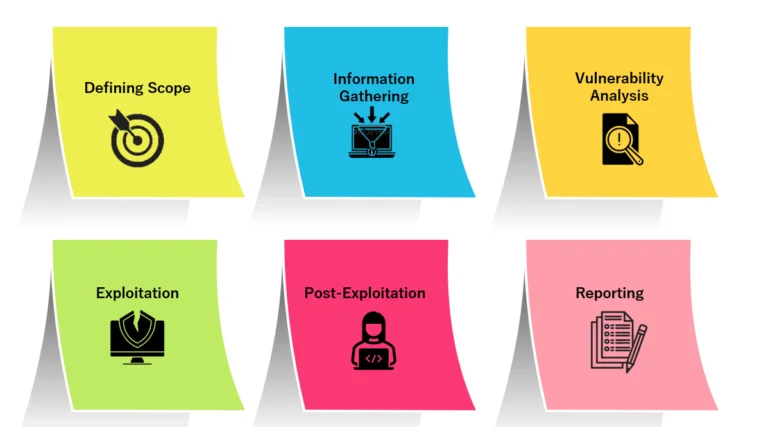
IMPORTANT ASPECT OF DOING PENETRATION TESTING
Penetration Testing Tools in UAE empower organizations to assess and strengthen their cybersecurity posture through regular testing. These tools help evaluate how well existing security controls protect against evolving threats. To conduct an effective penetration test, organizations should consider the following key aspects:
1. Scope Definition
Clearly define the scope of the test. Specify the systems, applications, and networks to be tested. Decide on the testing approach—such as white-box, black-box, or grey-box testing—and outline any limitations or constraints.
2. Preparation
Prepare the environment before testing begins. Ensure system backups are in place and isolate the testing environment from live production systems to prevent service disruptions or data loss.
3. Testing Methodology
Select a well-established methodology, such as the OWASP Testing Guide, to guide the testing process. Document each step, from information gathering to exploitation and post-exploitation phases, to maintain a structured and repeatable testing process.
4. Tool Selection and Configuration
Use reliable penetration testing tools in UAE that suit the scope of your test. Keep all tools updated and configure them properly to ensure accurate results. Popular tools include:
-
Nmap for network discovery and mapping
-
Metasploit for exploiting known vulnerabilities
-
Burp Suite for web application testing
-
Wireshark for traffic analysis
-
Nessus for vulnerability scanning
5. Ethical and Legal Compliance
Ensure all activities align with ethical hacking principles and comply with UAE cybersecurity laws. Obtain proper authorization from system owners before starting the test.
6. Effective Communication
Establish communication protocols between penetration testers, security teams, and system owners. Regular updates and approvals help manage expectations and reduce risks during the testing process.
7. Thorough Documentation
Record every step of the penetration test. Include details such as:
-
Tools and techniques used
-
Vulnerabilities discovered
-
Systems impacted
This documentation becomes essential for verifying findings, replicating results, and supporting remediation.
8. Actionable Reporting
Deliver a detailed and easy-to-understand report after the test. Highlight the most critical vulnerabilities, potential impacts, and recommend prioritized remediation steps. A well-structured report should include:
-
Executive summary
-
Risk ratings
-
Technical findings
-
Screenshots and evidence
-
Remediation guidance
9. Collaborative Remediation
Work closely with IT teams and stakeholders to fix identified vulnerabilities. Provide technical support and verify that patches and configuration changes effectively resolve the issues.
10. Ongoing Follow-Up
Schedule follow-up tests to confirm that remediation efforts succeeded. Regular penetration testing also helps maintain a strong security posture over time and adapts to emerging threats.
Unlock the possibilities today! Explore our wide range of services and get in touch with us at Contact us or email us at [email protected] to discover how we can cater to your needs.
You can also call us at +971-585-778-145 or whatsapp
A: Penetration testing (pen test) is a simulated cyberattack against your systems, applications, or network performed by security experts to find vulnerabilities before attackers do.
A: It reveals real-world risks, helps prioritise fixes, reduces breach likelihood, and proves security controls work under attack.
A: Best practice is at least once a year and after major changes (new apps, architecture changes, or significant third-party integrations). High-risk environments may test more frequently.
A: Common types: network (external/internal), web application, mobile app, API, wireless, cloud, social engineering, and physical penetration tests.
A: A vulnerability scan is automated and lists potential issues. Penetration testing is hands-on — testers exploit weaknesses to show real impact and proof of concept.
A: Black-box: tester has no internal info (mimics external attacker). White-box: full access to source/configs (in-depth). Grey-box: limited internal info (balanced approach).
A: Phases: scoping, information gathering, vulnerability discovery, exploitation (safe), post-exploitation analysis, reporting, and remediation verification (re-test if needed).
A: Executive summary, technical findings (vulnerabilities, proof of concept), risk ratings, impact assessment, step-by-step remediation guidance, and retest recommendations.
A: Tests can affect systems if not carefully planned. A reputable provider will define rules of engagement, schedule safe windows, and use non-destructive techniques when required.
A: Identify assets, appoint contacts, document test windows, whitelist tester IPs if needed, back up critical systems, and decide the test scope and depth in advance.
A: It depends on scope. Credentialed (authenticated) tests reveal internal flaws missed by unauthenticated tests. Many clients run both types for coverage.
A: A technical lead (sysadmin/DevOps), an operations contact for incidents, and a project owner for approvals and post-test remediation tracking.
A: Costs vary widely by scope, complexity, and provider — from a few hundred dollars for small web app checks to tens of thousands for full enterprise assessments. Get a scope-based quote.
A: Small web app tests can take 2–5 days; medium scopes 1–3 weeks; large enterprise engagements may run several weeks. The timeline depends on complexity and depth.
A: Prioritize by risk (impact and exploitability), apply patches or configuration changes, perform code fixes for application issues, and validate with a retest.
A: Yes — retesting confirms fixes are effective and that remediation didn’t introduce new issues.
A: Yes. Many regulations and standards (PCI DSS, ISO 27001, HIPAA, etc.) require or recommend periodic penetration testing as part of an overall security program.
A: Always use authorized tests with written permission (rules of engagement). Unauthorized testing can be illegal and may cause service disruptions or data loss.

