Vulnerability Assessment
Vulnerability assessment is the process of identifying, analyzing, and prioritizing security vulnerabilities in a system, network, or application.

Know Your Weaknesses Before They’re Exploited – Eshield Comprehensive Vulnerability Assessment
What is Vulnerability Assessment
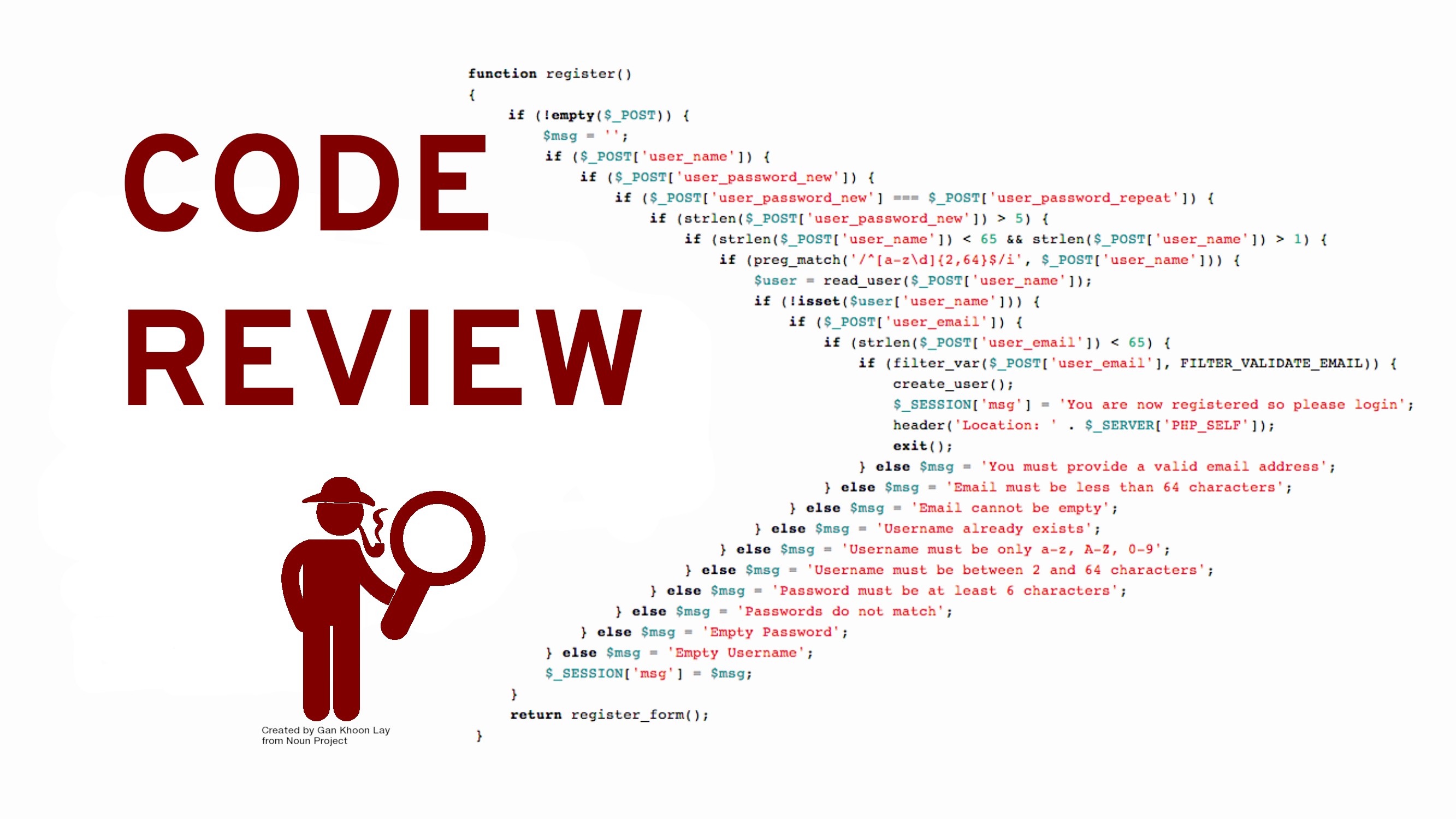
Data Vulnerability assessment is a methodical process of detecting and assessing vulnerabilities in a system, network, application, or infrastructure. Moreover, it entails the use of numerous tools and techniques to assess the security posture and find vulnerabilities that attackers could exploit.
A vulnerability assessment’s primary goal is to proactively identify vulnerabilities and assess their potential impact on system security. Furthermore, this process assists organizations in understanding their risk exposure and making informed risk mitigation and security decisions. There are many applications that can help in automated IT Vulnerability Assessment like Nessus.
Benefits of performing Vulnerability Assessment
-
Improved Security:
It aids in the identification of potential security issues and provides guidance on how to minimize them. Additionally, organizations can strengthen their security posture and lower the risk of cyberattacks by fixing these vulnerabilities.
-
Savings on costs:
It can assist in detecting potential security issues and providing recommendations on how to reduce them. Therefore, by addressing these vulnerabilities, organizations can prevent the expenses of a data breach. Such data breaches include legal bills, reputation harm, and business loss.
-
Compliance:
Many regulatory frameworks require organizations to do vulnerability analytics on a regular basis. Moreover, organizations can assure compliance with these rules by undertaking these assessments.
-
Improved Decision Making:
Vulnerability assessments give organizations with insights into potential security issues, allowing them to make informed decisions about how to strengthen their security posture.
Our Methodology
-
Planning:
The first step in vulnerability assessment is planning. Thus, it involves identifying the assets that need to be assessed, the scope of the assessment, and the objectives of the assessment.
-
Gathering information:
This includes identifying the assets that need to be assessed, understanding the system architecture and network topology, and identifying potential threat sources.
-
Vulnerability scanning:
This involves using automated security scanning software tools the system or network for known vulnerabilities, such as outdated software, misconfigured systems, and known security flaws.
-
Vulnerability analysis:
This involves analyzing the results of the web vulnerability testing to determine the severity of each vulnerability and the potential impact on the system.
-
Risk assessment:
This involves evaluating the likelihood and potential impact of each vulnerability and prioritizing them based on their level of risk.
-
Reporting:
This involves documenting the findings including the vulnerability score and mitigation method.
Services we provide!
Vulnerability Scanning

IT infrastructure

Software testing tools