Why is Cybersecurity Essential in the Digital Transformation Landscape?
Protecting sensitive data:
As companies undergo digital transformation, they are storing more and more data digitally, making them vulnerable to cyber-attacks. Ensuring the security of this data is essential to protect customer information and maintain trust.
Compliance with regulations:
With the increase in cyber threats, governments and regulatory bodies have introduced strict guidelines and regulations for businesses to follow. Failure to comply with these regulations can result in significant penalties and damage to the company’s reputation.


Safeguarding intellectual property:
Digital transformation often involves the use of new technologies and innovations that are considered trade secrets or intellectual property. Without strong cybersecurity measures in place, these valuable assets can be stolen or compromised by cyber criminals.
Business continuity:
In the event of a cyber attack or data breach, businesses can face significant downtime and financial losses. By implementing cybersecurity measures, companies can reduce the risk of disruptions to their operations and ensure business continuity.


Protection against ransomware:
Ransomware attacks have become increasingly common in recent years, with cyber criminals demanding payment in exchange for releasing encrypted data. Implementing strong cybersecurity measures can help protect businesses from falling victim to these types of attacks.
How Can Businesses Prioritize Cybersecurity during Digital Transformation?
1. Implement a cybersecurity culture:
Make cybersecurity a top priority within the organization by creating a culture that promotes awareness and best practices among employees at all levels.


2. Conduct regular risk assessments:
Identify potential vulnerabilities and evaluate the risks associated with digital transformation initiatives to develop a comprehensive cybersecurity strategy.
3. Invest in cybersecurity tools and technologies:
Deploy security solutions such as firewalls, antivirus software, encryption, and multi-factor authentication to protect data and systems from cyber threats.


4. Train employees on cybersecurity best practices:
Provide ongoing training and education to staff on how to recognize and respond to security threats, including phishing attacks, malware, and social engineering tactics.
5. Establish incident response and recovery plans:
Develop protocols for detecting and responding to security incidents, as well as plans for recovering data and systems in the event of a breach.
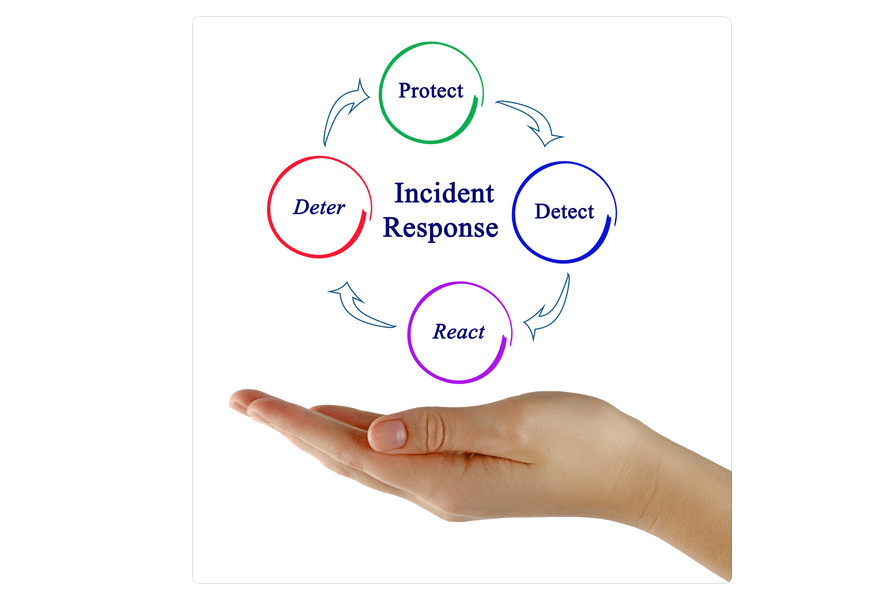

6. Collaborate with cybersecurity experts:
Seek guidance from cybersecurity experts and consultants to ensure that the organization is following best practices and staying ahead of emerging threats.
7. Stay updated on cybersecurity trends:
Monitor industry developments and stay informed about new cybersecurity threats, regulations, and technologies to continuously improve the organization’s security posture.

What Are the Latest Trends in Cybersecurity and Digital Transformation?

1. Zero Trust Security:
This approach assumes that every user or device attempting to access a network is a potential threat and therefore requires strict verification before granting access.
2. Artificial Intelligence and Machine Learning:
These technologies are being used to detect and respond to threats in real-time, as well as automate security operations to reduce the burden on human analysts.


3. Cloud Security:
As more organizations move their data and workloads to the cloud, there is an increasing focus on securing these environments and implementing robust cloud security measures.
4. Identity and Access Management (IAM):
With the increasing number of devices and users accessing company networks, IAM solutions are becoming essential for managing and controlling access to sensitive data and resources.


5. DevSecOps:
This approach integrates security into the software development process, ensuring that security measures are built into applications from the very beginning.
6. Endpoint Security:
With the rise of remote work and the proliferation of mobile devices, securing endpoints such as laptops, smartphones, and tablets has become a top priority for organizations.


7. Cybersecurity Training and Awareness:
As cyber threats continue to evolve, organizations are investing more in employee training and awareness programs to educate users about potential risks and how to prevent cyber attacks.
8. Data Privacy and Compliance:
With the increasing number of data breaches and regulations such as GDPR and CCPA, organizations are focusing on ensuring the security and privacy of customer data to maintain compliance with these laws.

Our Services

such as network security, email security, cloud security, endpoint security, and consulting services to protect businesses from cyber threats. Their team of experienced professionals works tirelessly to ensure that clients have the most up-to-date and effective cyber security measures in place to safeguard their sensitive data and information. With eShield IT Service, businesses can rest assured that their cyber security needs are being met and their systems are protected from potential cyber-attacks.











