In this article we will be diving deep about this interesting topic Third Party Risk Management.
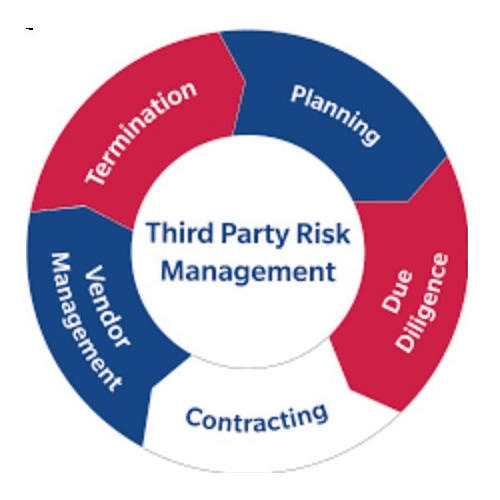
Now, let us see what it means !
Third-Party Risk Management : What Is It ?
– There are many dangers involved in establishing and maintaining connections with third parties.
– Regardless of the size of your company, you almost certainly have business partnerships with numerous third parties for certain kinds of operations. Operational data and confidential information are prone to abuse and exploitation when they are shared with other parties. This is where danger enters the picture.
– Building and sustaining a third-party risk management policy is an essential business decision when these third parties lack reliable cybersecurity protections or compliance.
– Identification, assessment, and control of all the many risks that may arise over the whole lifecycle of your connections with third parties are all part of the Third-Party Risk Management (TPRM) process. TPRM frequently starts at the procurement phase and should continue through the offboarding procedure.
– There are several potential hazards that could have a significant impact, including reputational, strategic, managerial, and financial threats. Data compromise, unauthorized third-party use of information, the negative and harmful repercussions of non-compliance, and anomalies in supply chain management are more particular hazards.
Why is TPRM crucial?
– Today’s hot issue is third-party risk management. Just consider how practically every organization’s supply chain has evolved, particularly in light of the digital transformation implemented to suit the demands of a changing workforce. There are numerous new businesses with which we interact, including new cloud providers, hosting providers, vendors, and suppliers.
– Even third parties that you have dealt with on a regular basis pose a security concern. Take a look at the historic Target breach from 2013 to see how the attackers were successful because a third-party HVAC vendor employee of Target opened a phishing email and stole credentials.
– The HVAC vendor in this instance had more access to Target’s networks than was necessary. This danger is reduced by TPRM. Additionally, almost all compliance guidelines today specify the necessity of ongoing oversight of your third-party supply chain.
– Let’s face it: Companies far too frequently elect to believe their vendors when they say they are secure. They might be in various instances. But how can you control access to your network or sensitive data when there are so many vendors coming and going from our company?
– The following are some typical questions you should ask about TPRM :
– What kind of information do third parties access ? What type of access?
– Have you given them physical access?
– What would occur if the third party’s accessibility were to be jeopardized ? How would that
– impact your business? What would happen?
– How would it affect you if they leaked some of your private information ?
What Distinguishes a Third Party from a Fourth Party ?
A fourth-party is the third-party of your third party, whereas a third-party is a supplier, vendor, partner, or other organization conducting business directly with your company. Fourth parties, often known as “Nth parties,” refer to connections made through third parties between parties farther down the supply chain who are not necessarily contractually obligated to your firm.
TPRM obstacles must be addressed and solutions
– Today, it is difficult to handle third-party risk internally. When you start to approach TRPM manually, it becomes a very resource-intensive operation.
– Take into account the difficulties, such as :
– Inadequate resources
– Long list of third parties
– Several evaluation methods
– Communicating about problems
– A wide range of compliance criteria
– Both parties experience ongoing transformation
– Workflow automation is lacking
There are five steps to managing third-party risks
– No matter how you choose to approach TPRM, there are five crucial measures that will significantly reduce risk.
1. **Identify -** The first step is figuring out which businesses you do business with pose any kind of risk. It’s crucial to comprehend this ecology of third parties.
2. **Classify -** Using a risk-based methodology, you must determine the level of risk that each third party poses to your company based on the data, system access, and service they offer.
3. **Assess -** Next, you must assess the third parties you do business with in terms of their security posture. You’ll have different levels of confidence based on third-party risk depending on the type of your firm.
4. **Manage Risk -** In this section, you’ll lay out the processes to implement policies and choose how to handle remediation. In essence, you’re deciding whether to take chances or not.
5. **Monitor -** The final stage entails continuing to keep an eye on third parties to make sure they uphold their security posture and fulfil their contractual responsibilities.
Why use services for managed third-party risk management?
– You don’t have to do everything yourself, even though TPRM can seem overwhelming. Your TPRM program can be managed for you by a number of highly skilled and competent businesses.
– Your TPRM requirements will differ depending on your organization. You could only need a one-time report or a point-in-time assessment. Alternatively, you might gain from ongoing monitoring and alerting of issues found with a third party’s security posture.
– Utilizing cutting-edge solutions like FortifyData, managed TPRM may evaluate your third parties by assigning them a score that matches a FICO credit score while taking into account people, processes, and technology.
– Going a step further, TPRM-as-a-service enables enterprises to achieve optimal TPRM (TPRMaaS). All crucial facets of third-party risk management are taken care of by a team of professionals using TPRMaaS.
– They can assist you by :
– Throughout the relationship lifespan, control third-party processes.
– Embrace outside businesses
– Create risk profiles and classifications for third parties.
– Offer third-party evaluations
– Manage workflow and provide outside oversight
– Reports currently available and ongoing updates
– Continuously keep an eye on important third parties
Who Owns TPRM in this Department?
– Third-party risk management does not have a one-size-fits-all strategy. There isn’t a fixed department that is in charge of managing vendor risk because every business is unique. A team for managing vendor risks or third-party risks may exist in certain established firms, although this is not the case for many. Therefore, typical positions and divisions that “own” third-party risk include:
– Chief Information Security Officer (ciso)
– Director of Procurement (CPO)
– Information Officer in Chief (CIO)
– Director of Privacy (CPO)
– Technology Information (IT)
– Purchasing and Sourcing
– Security of Information
– Risk and adherence
– Supply Chain Supervisor
– Manager of Third-Party Risk
– Manager of Vendor Risk
– Vendor Administration
– Contract Manager
Conclusion
That’s all about the Third party Risk Management. After reading this essay, I hope you found it enjoyable and learned something new. We have learned what is it, how crucial it is, why do we need it, steps involved in managing third-party risks, departments owning the TRPM.

