In this article we will be diving deep about this interesting topic Incident Handling and Response.
Now, let us see what it means !
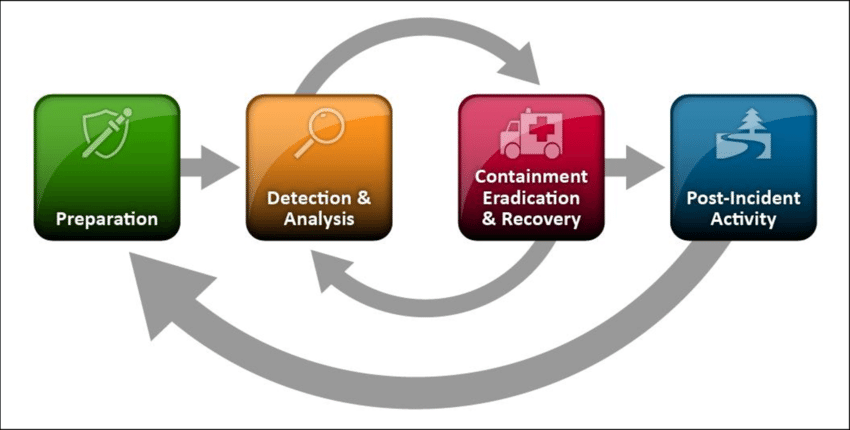
Defining Incident Response
Incident response is a systematic approach of dealing with various types of security incidents, cyber threats, and data breaches. The purpose of incident response is to locate, contain, and limit the cost of a cyberattack or live incident.
A well-designed incident response (IR) plan can address a possible vulnerability and help avoid future assaults, but it is not the end-all solution. Response is a subset of Incident Handling, which examines the logistics, communications, synchrony, and preparation necessary to resolve an incident.
The Computer Security Incident Response Team (CSIRT) and the Security Operation Center are usually in charge of this type of activity. While incident management is at the center of the CSIRT’s role, reporting, analysis, and response are all included.
Prior to these stages, however, it is critical that the incidence be discovered and reported promptly. It is at this point that the role of a SOC Analyst becomes critical. All of this is best taught in EC-Incident Council’s Handling Program, which was created by some of the greatest practitioners in the business.
Now, let us understand why do we need it !
Need of Incident Response
Data breaches cause operational downtime, reputational damage, and financial loss for businesses. Any vulnerability grows more dangerous the longer it remains in a system. For the majority of organizations, a security breach leads in a drop in stock value and a loss of customer trust for the majority of businesses. Companies need a well-planned cybersecurity incident response plan to eliminate such risks, which attempts to do the following.
– Getting back to normal business operations
– Maintaining a low level of financial and reputational harm
– Identifying and responding to cyber threats in a thorough and timely manner
– To avert such attacks, the security posture must be strengthened
Another significant goal is to integrate the security posture with regulatory requirements. To avoid significant fines and penalties, businesses should adhere to these guidelines. The following are a handful of the most important acts and regulations:
HIPPA (for health purpose)
The Health Insurance Portability and Accountability Act (HIPAA) was created to protect electronic Protected Health Information (PHI). When a healthcare organization is HIPAA compliant, it follows the HIPAA Security Rule and ensures that administrative, technical, and physical measures are in place to secure sensitive personal and health information.
PCI DSS (for payments purpose)
The Payment Card Industry Data Security Standard (PCI DSS) is a security standard aimed at preventing data theft and fraud in credit and debit card transactions. Despite the fact that PCI DSS compliance is not required, businesses should follow the standards to ensure the security of their credit and debit card transactions. Being PCI DSS compliant aids in the development of trust among stakeholders and customers.
Gram-Leach-Bliley Act (for financial purpose)
The Gramm–Leach–Bliley Act (GLBA) is a law that helps to improve industrial competition. Its major goal is to secure client data security and confidentiality, as well as data integrity through protection against potential cyber threats and unauthorized access and correct data disposal.
FISMA (for federal purpose)
The Federal Information Security Management Act (FISMA) is a broad framework that applies to federal entities in the United States. The statute safeguards government data, operations, and assets from natural disasters and cyberattacks.
Type Of Incidents
The following are a few examples of different types of occurrences.
Phishing attacks
At the start of 2020, there will be a 350 percent increase in phishing websites, according to the United Nations.
Denial-of-Service attacks
DDoS attacks against utilities have increased by 595 percent year over year, according to NETSCOUT.
Ransomware attacks
Within six months, there was a 20% increase in ransomware attacks, totaling 121.4 million incidents. SonicWall (SonicWall)
SQL injections
SQL Injection assaults have increased by 8000 percent in 2019 compared to 2018 – WatchGuard
Malware attacks
New malware attacks disguised as Microsoft Office file formats have increased by 176 percent, according to SonicWall.
Now, let us see the differences in Incident Handling, Incident Response and Incident Management !
The Variations
Incident Response
It’s a set of technical procedures for analyzing, detecting, defending against, and responding to an incident. It’s a step in the incident response and management process. It is frequently used in conjunction with the term incident management.
Incident Management
Both incident management and incident response are intertwined. It’s common to think of it as a single function that makes processes go more smoothly. In this case, incident management comes into play. Incident management entails bringing together both incident response and incident handling to enable a seamless procedure from reporting an issue to planning and resolving it.
Incident Handling
It is the predefined method and procedures for dealing with an incident. Before, during, and after an incident is recognized, it includes the planning and actionable stages.
Incident Response Plan
When an IR plan is activated, the BCP for continued business operations is also activated. Both incident handlers and BCP team leaders require quick and accurate information in order to take appropriate action in the case of an unexpected occurrence. The aspects of incident management systems listed below assist in ensuring good company continuity.
Initial Response Statistics
Employees want crucial information in a real-time environment for initial response statistics. This information aids incident responders in quickly resolving escalating situations. It’s critical for incident management to be able to set up an intuitive, adaptable system.
Reporting
Only if incident managers have reliable information can they take adequate action against a computer security problem. To customize an effective reaction, this method requires real-time details of the situation.
Feedback
After the event has been resolved, honest feedback from stakeholders can help to improve the current incident management system.
Incident Response Process
A company’s ability to stay in business is aided by an incident response process. It’s a collection of methods aimed at detecting, assessing, and responding to potential security threats. The procedure’ main goal is to reduce the impact and provide a quick recovery.
Incident response technique, in basic terms, deals with security incidents, breaches, and potential cyber threats. It includes an incident response strategy for detecting a cyber-attack, minimizing its damage, and lowering the financial cost.
This process basically follows OODA.
Observe
Constant security monitoring aids in the detection of unusual network/system activities.
Orient
An assessment of the organization’s cyber danger landscape. To prioritize security issues, logically connect and bring out real-time context.
Decide
Determine an action plan based on observations and context that provides the least amount of downtime and the quickest system recovery.
Act
Clean-up, rehabilitation, and recording lessons learned for future reference
Paraphrase’s Defined By NIST For Incident Response
Identify
Developing organizational awareness of various security concerns relating to systems, information assets, data, and operations
Protect
Developing and implementing appropriate protections to improve critical infrastructure service delivery
Detect
Processes for detecting security incidents are being developed and implemented.
Respond
Developing and implementing methods to deal with the incidents that have been discovered.
Recover
Creating and implementing a plan to get the firm back up and running following the incident.
5 – Step Process of Incident Response
Determining critical points
Replicate your organizational data and store it in a remote location to avert major losses. Because business networks are complicated, keep track of backup locations so that IT workers can swiftly restore the network if necessary.
Identifying point of failure
Create a plan to secure the important components once you’ve identified them. The network as a whole can be jeopardized by single points of failure. As a result, include software failover features and other necessary tools in your solution.
Developing continuity plan
Some sites or procedures may become inoperable or unavailable as a result of a disaster or a security breach, but this should not have an impact on routine business operations or personnel security. Create a strategy that includes virtual private networks (VPNs) and secure online gateways to allow employees to continue working without interruption.
Establishing cyber sec response plan
Create a written strategy that includes a list of incident responder roles and duties, tools and technologies used, and effective data recovery procedures.
Training
Every employee should be well-versed in the various forms of cyberattacks and how to defend against them.
Conclusion
That’s all about the Incident Handling and Response. After reading this essay, I hope you found it enjoyable and learned something new. We have learned what is Incident Handling and Response, it’s need, types, their variations, about incident response plan,, their phases, and the 5-step process.

