Is Biometrics Secure
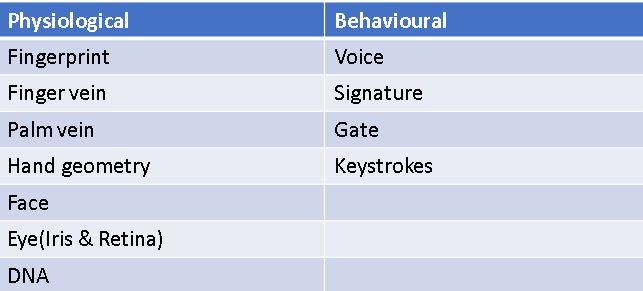
Biometrics are used everywhere. Biometrics are becoming an important part of our life, we use it everywhere, from smartphones to smart houses, from private offices to schools and businesses, and many other places where there is a need for identification. Biometrics can be of any form, be it physical or behavioral. Various biometric technologies are available for identifying or verifying an individual by measuring fingerprint, hand, face, signature, voice, or a combination of these traits. These include anything that can be measured and calculated, biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. In this report, we will try to find how strong biometrics are. I will explore a number of possibilities that are possible with biometrics and give detailed data. In the end, I will give my conclusion on this, whether it is an effective form of identification or not. Moreover, this paper will give you a proper idea about the future of biometrics
Introduction
A biometric system is a system that is basically a pattern recognition system that is operated by collecting biometric data from an individual, via extracting a set of data from the collected data and comparing the extracted set of data with the saved data in the database. Biometrics system is used to measure individuals’ unique behavioral or physical characteristics to authenticate or recognize their identity.
Stages
The biometric system is divided into two stages: the enrollment module and the identification module.
Stage 1:
The first time a user enters his/her biometrics it is called enrolment. The user has to give his/her biometric data a number of times so that the software responsible for taking the biometrics can reconfirm the data and store it in the database.
Stage 2:
When the person tries to identify himself that is called an identification module.
Why Biometrics
The installation of biometrics involves a huge investment at first but it doesn’t have high maintenance charges. Due to the introduction of the Aadhar fingerprint scanner is easily available in India nowadays. In India biometrics is used as a form of authentication in Aadhar cards, and passports, and in aadhar linked bank accounts fingerprint is used to withdraw money. For buying a sim card we need aadhar card i.e. we have to give our biometrics. Due to these reasons, biometrics has become a very important liability that we need to keep it safe so that it doesn’t fall into the wrong hands. Moreover, if your password gets public it can be changed but biometrics can’t be changed let’s take a fingerprint as an example fingerprint can’t change throughout life it can be light and ineffective due to manual labor with hands but it can’t be changed.
The most common form of biometric we use is the fingerprint. It is used in a lot of places like mobile phones, offices, and smart houses. Biometrics has become an integral part of our life but there are lots of problems with biometrics.
An early attack on fingerprint biometric authentication was called the gummy bear hack, and it dates back to 2002 when Japanese researchers, using gelatin-based confection, showed that an attacker could lift a latent fingerprint from a glossy surface, the capacitance of gelatin is similar to that of a human finger, so fingerprint scanners designed to detect capacitance would be fooled by the gelatin transfer.
Benefits Of biometrics
- It’s faster and more convenient for users (no need to remember passwords that’s the reason people use it the most)
- Strong authentication since biological characteristics are distinct i.e. no two people can have the same fingerprint and for iris, it’s far more impossible because it has far more details.
- Eliminates friction associated with traditional security measures i.e. two people can have the same password but they can’t have the same biometrics.
- Biometrics is the type of authentication system that can’t be guessed or brute forced.
Disadvantages of Biometrics:
Despite the features there are many disadvantages in biometrics the disadvantages are as follows:-
- Costs –A one-time huge investment is needed in biometrics for security.
- Data breaches – Biometric databases can still be hacked and the biggest problem is once your biometric data is lost it’s lost as you can’t change your biometric data.
- Tracking and data – Biometric devices like facial recognition systems can limit privacy for users.
- Bias – Machine learning and algorithms must be very advanced to minimize biometric demographic bias.
- False positives and inaccuracy – False rejects and false accepts can still occur preventing select users from accessing systems.
But besides all the disadvantages we still want to use biometrics as the advantages supersede the disadvantages.
Observation
The main problem behind fingerprints is they can be created easily i.e. for office attendance or in any private company people use fake fingerprints to mark their attendance or in places like that and collecting fingerprint data isn’t hard it can be collected even from a cup or even from a picture as well. A hacker named Jan Krissler cracked the iPhone 5s fingerprint within 24 hrs of its launch. In 2015, That same person recreated the fingerprint of a German Defence Minister from a photograph. To show how easy this is to create a fake fingerprint we can just do a Google search with the keyword “How to create a fake fingerprint ” and we will get a step-by-step process that can be followed by even kids so when we use the fingerprint-based password in our phone it will be very easy for anyone around us to get access to your files.
The next Biometrics most used is the iris scanner. Iris scanner is far more complicated to be duplicated but it possesses a far more dangerous threat that it can be bypassed by anyone who has access to a very high-quality image of our eyes. Moreover, it can be opened by someone mistakenly. Other than that we have a face as a form of authentication but the earlier versions of face unlock available in phones could have been easily cracked by using a picture or by a similar-looking family member, even if a person is sleeping his face can be used without his permission.
Conclusion
Biometrics itself can not be used as any form of authentication at any important place because it isn’t strong enough and can be cracked by fake biometrics or by other means. But biometrics can be used as a part of multi-factor authentication, it can be used as an extra layer of encryption. Biometrics (fingerprint or iris scanner) can be paired with a pin or password to use as a means of authentication or sometimes it can be used with a different form of authentication like cards or RFID cards.
Please visit our Services page for a full range of services offered.